图灵盾SDK官方给出的检测能力:
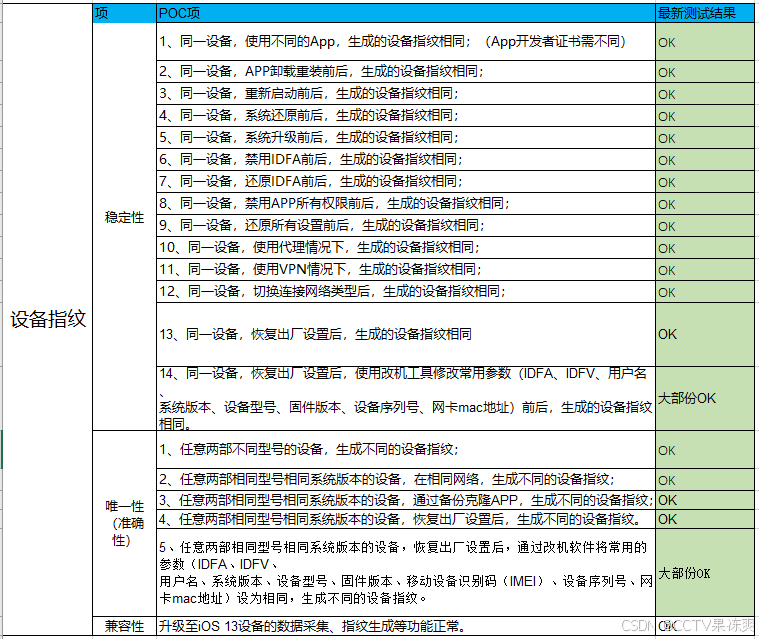
1)设备指纹
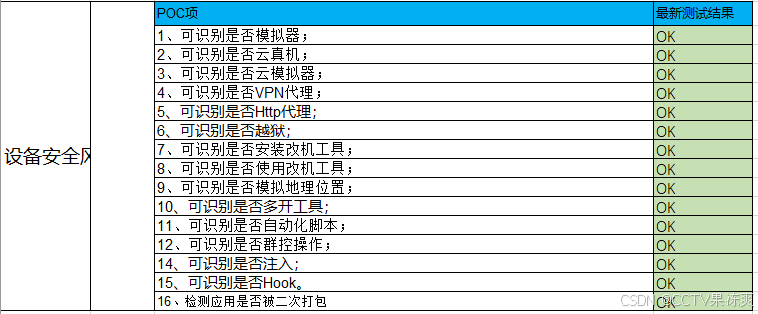
2)风险识别:
 逆向分析
逆向分析
1、数据组织和上报
a) 数据上报方式:HTTPS协议上报
b) 数据内容:序列化后的二进制再加密。
c) 数据内存保存形式:C结构体自定义JSON数据,key为整数
JSON数据Value值dump如下:
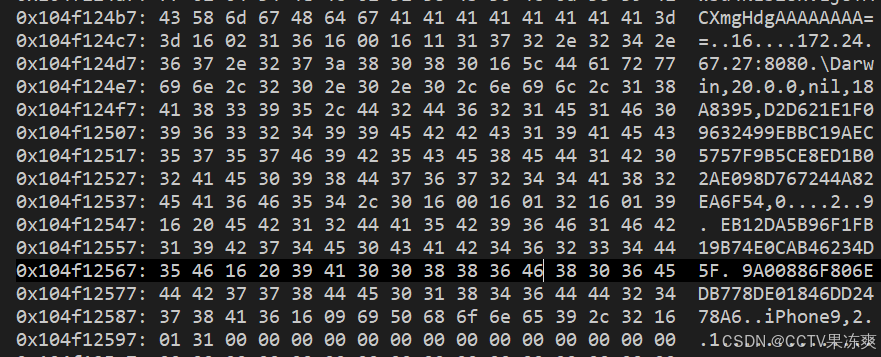
{ 1006 = 127968497664; 1012 = ""; 1024 = CN; // 地区 1036 = ""; 1042 = ""; 1054 = 0; 1001 = "00000000-0000-0000-0000-000000000000"; // IDFA 1007 = 2749054976; // 内存大小 1013 = 2; // 网络状态,1 , 2 1019 = 16; // 越狱状态值 1025 = 460; 1037 = ""; 1049 = EB12DA5B96F1FB19B74E0CAB46234D5F; //entitlement md5 1055 = 2; // 充电状态 1002 = "41907083-B606-4047-8814-11CB24BB48DE"; // vendorIdentifier 1008 = "0.6820670366287231"; // brightness 屏幕亮度 1014 = ""; // 路由器 ssid 1020 = "iPhone9,2"; 1026 = 01; 1038 = ""; // 签名段二进制数据base64 1044 = "MIAGCSqGSIb3DQEHAqCAMIACAQExDzANBglghkgBZQMEAgEFADCABgkqhkiG9w0BBwEAAKCCDvIwggRRMIIDOaADAgECAhB8r2kKJbc5/nubRHrBeMXuMA0GCSqGSIb3DQEBCwUAMGIxCzAJBgNVBAYTAlVTMRMwEQYDVQQKEwpBcHBsZSBJbmMuMSYwJAYDVQQLEx1BcHBsZSBDZXJ0aWZpY2F0aW9uIEF1dGhvcml0eTEWMBQGA1UEAxMNQXBwbGUgUm9vdCBDQTAeFw0yMDAyMTkxODEzNDdaFw0zMDAyMjAwMDAwMDBaMHUxRDBCBgNVBAMMO0FwcGxlIFdvcmxkd2lkZSBEZXZlbG9wZXIgUmVsYXRpb25zIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MQswCQYDVQQLDAJHMzETMBEGA1UECgwKQXBwbGUgSW5jLjELMAkGA1UEBhMCVVMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDY9Yn8qFkLh8dMkS4tVpDTeB2kMOmlSO8LQ78thPskXUUb5etZNhJcVGSebGIttMaXysw89tYGkfzlAqYcarR51WfLrOk/BxHhhLxHHWaOOaLotEntOtLhEGB6jpOMysDaDMCD0OP5kdanjMjBc+KuRtFinZKokGA3fWiWzY3g/Jv6eLvje68tF91b/oBZI3UXuBLB7RvlNM7+IrWeSbDlVb+PhKI8qLrFhpUW5ADJnwPQzLM6FnvWBVyd60euDbUtjA5pTUDQS0w7BJ6NIbGsLkNUMM7BioaUmEvfag0//vscrpcXwngKMOBfH1Q7SbclABo3gtJWl6VSSXxgOJvvAgMBAAGjge8wgewwEgYDVR0TAQH/BAgwBgEB/wIBADAfBgNVHSMEGDAWgBQr0GlHlHYJ/vRrjS5ApvdHTX8IXjBEBggrBgEFBQcBAQQ4MDYwNAYIKwYBBQUHMAGGKGh0dHA6Ly9vY3NwLmFwcGxlLmNvbS9vY3NwMDMtYXBwbGVyb290Y2EwLgYDVR0fBCcwJTAjoCGgH4YdaHR0cDovL2NybC5hcHBsZS5jb20vcm9vdC5jcmwwHQYDVR0OBBYEFAn+wBWQ+a9kCpISuSYoYwyX7KeyMA4GA1UdDwEB/wQEAwIBBjAQBgoqhkiG92NkBgIBBAIFADANBgkqhkiG9w0BAQsFAAOCAQEArWUT6PbggXdEAkdCvl+lOSDqYqn9xZDJcxPVnpvQqg+NjcvtAc9sKEBbx1UkQfj8z8G1I+nc7PFvyoAdd8LEYUklZ68PyjklrdPjeswzKA0OLqFXQHP65lyuBlEp7eOFDE9h3DIWi3fQRMpdcgMxRpyum0Aa+vTg0z76L4xmn5fEVFnv0kj0B5lJYFkZx92U0cDBbH94Ie8M6ztsmYJLUmA4tTmCbexSMVO+D5FMSUl0j6ZRy4RHTh11J269+dJc83/CbAsJNuJk5MI3AxQZ1epqlKqp2/72mghni+8ruKoXSYOvz8u86c/qlXGwtEWizOWHqgrDQTp5XNpQNJ2VOzCCBLswggOjoAMCAQICAQIwDQYJKoZIhvcNAQEFBQAwYjELMAkGA1UEBhMCVVMxEzARBgNVBAoTCkFwcGxlIEluYy4xJjAkBgNVBAsTHUFwcGxlIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MRYwFAYDVQQDEw1BcHBsZSBSb290IENBMB4XDTA2MDQyNTIxNDAzNloXDTM1MDIwOTIxNDAzNlowYjELMAkGA1UEBhMCVVMxEzARBgNVBAoTCkFwcGxlIEluYy4xJjAkBgNVBAsTHUFwcGxlIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MRYwFAYDVQQDEw1BcHBsZSBSb290IENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA5JGpCR+R2x5HUOsF7V55hC3rNqJXTFXsixmJ3vlLbPUHqyIwAugYPvhQCdN/QaiY+dHKZpwkaxHQo7vkGyrDH5WeegykR4tb1BY3M8vED03OFGnRyRly9V0O1X9fm/IlA7pVj01dDfFkNSMVSxVZHbOU9/acns9QusFYUGePCLQg98usLCBvcLY/ATCMt0PPD5098ytJKBrI/s61uQ7ZXhzWyz21Oq30Dw4AkguxIRYudNU8DdtiFqujcZJHU1XBry9Bs/j743DN5qNMRX4fTGtQlkGJxHRiCxCDQYczioGxMFjsWgQyjGizjx3eZXP/Z15lvEnYdp8zFGWhd5TJLQIDAQABo4IBejCCAXYwDgYDVR0PAQH/BAQDAgEGMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0OBBYEFCvQaUeUdgn+9GuNLkCm90dNfwheMB8GA1UdIwQYMBaAFCvQaUeUdgn+9GuNLkCm90dNfwheMIIBEQYDVR0gBIIBCDCCAQQwggEABgkqhkiG92NkBQEwgfIwKgYIKwYBBQUHAgEWHmh0dHBzOi8vd3d3LmFwcGxlLmNvbS9hcHBsZWNhLzCBwwYIKwYBBQUHAgIwgbYagbNSZWxpYW5jZSBvbiB0aGlzIGNlcnRpZmljYXRlIGJ5IGFueSBwYXJ0eSBhc3N1bWVzIGFjY2VwdGFuY2Ugb2YgdGhlIHRoZW4gYXBwbGljYWJsZSBzdGFuZGFyZCB0ZXJtcyBhbmQgY29uZGl0aW9ucyBvZiB1c2UsIGNlcnRpZmljYXRlIHBvbGljeSBhbmQgY2VydGlmaWNhdGlvbiBwcmFjdGljZSBzdGF0ZW1lbnRzLjANBgkqhkiG9w0BAQUFAAOCAQEAXDaZTC14t+2Mm9zzd5vydtJ3ME/BH4WDhRuZPUc38qmbQI4s1LGQEti+9HOb7tJkD8t5TzTYoj75eP9ryAfsfTmDi1Mg0zjEsb+aTwpr/yv8WacFCXwXQFYRHnTTt4sjO0ej1W8k4uvRt3DfD0XhJ8rxbXjt57UXF6jcfiI1yiXV2Q/Wa9SiJCMR96Gsj3OBYMYbWwkvkrL4REjwYDieFfU9JmcgijNq9w2Cz97roy/5U2pbZMBjM3f3OgcsVuvaDyEO2rpzGU+12TZ/wYdV2aeZuTJC+9jVcZ5+oVK3G72TQiQSKscPHbZNnF5jyEuAF1CqitXa5PzQCQc3sHV1ITCCBdowggTCoAMCAQICECrmQ26AkOQjQ0QoF0m4LkQwDQYJKoZIhvcNAQELBQAwdTFEMEIGA1UEAww7QXBwbGUgV29ybGR3aWRlIERldmVsb3BlciBSZWxhdGlvbnMgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkxCzAJBgNVBAsMAkczMRMwEQYDVQQKDApBcHBsZSBJbmMuMQswCQYDVQQGEwJVUzAeFw0yMDEwMjAwNzUxMzFaFw0yMzEwMjAwNzUxMzFaMIG1MRowGAYKCZImiZPyLGQBAQwKSEtCOFdQRkJSOTFEMEIGA1UEAww7aVBob25lIERpc3RyaWJ1dGlvbjogVGVuY2VudCBUZWNobm9sb2d5IChTaGVuemhlbikgQ28uLCBMdGQxEzARBgNVBAsMCkhLQjhXUEZCUjkxLzAtBgNVBAoMJlRlbmNlbnQgVGVjaG5vbG9neSAoU2hlbnpoZW4pIENvLiwgTHRkMQswCQYDVQQGEwJDTjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALuLOP2SfkuWFhpJWpQr58GbsQNwjKacdqQFFjlTxZr6aCvedoogSK4gyANLoGGKTzVeutrSW5zuO8NgnkZVRnyG3fQiLJr1VOWxOUINnxjNa8ci043HMFEWdKbxXZ0kFjpOzWsmM9UwsUcyRnjVi+HWFYC2IcLxqWV+HeI/MAj4dxbi4BsVt2iHtDjZWBSGKLnhiFDHAMCGSGHCGFOcFKN4FxFNlVX5IwLKs4WdiDEgYoh+tkxguqn1sC/HHKV5zANeIABRUoMf/EknfjhEV3ExHTVd2UagvO3zO1faeSkZOLsQEQlTOxFmEdOwpNuhGAEQWCnh5bTqYSlLM0EZc+kCAwEAAaOCAiMwggIfMAwGA1UdEwEB/wQCMAAwHwYDVR0jBBgwFoAUCf7AFZD5r2QKkhK5JihjDJfsp7IwcAYIKwYBBQUHAQEEZDBiMC0GCCsGAQUFBzAChiFodHRwOi8vY2VydHMuYXBwbGUuY29tL3d3ZHJnMy5kZXIwMQYIKwYBBQUHMAGGJWh0dHA6Ly9vY3NwLmFwcGxlLmNvbS9vY3NwMDMtd3dkcmczMDEwggEeBgNVHSAEggEVMIIBETCCAQ0GCSqGSIb3Y2QFATCB/zCBwwYIKwYBBQUHAgIwgbYMgbNSZWxpYW5jZSBvbiB0aGlzIGNlcnRpZmljYXRlIGJ5IGFueSBwYXJ0eSBhc3N1bWVzIGFjY2VwdGFuY2Ugb2YgdGhlIHRoZW4gYXBwbGljYWJsZSBzdGFuZGFyZCB0ZXJtcyBhbmQgY29uZGl0aW9ucyBvZiB1c2UsIGNlcnRpZmljYXRlIHBvbGljeSBhbmQgY2VydGlmaWNhdGlvbiBwcmFjdGljZSBzdGF0ZW1lbnRzLjA3BggrBgEFBQcCARYraHR0cHM6Ly93d3cuYXBwbGUuY29tL2NlcnRpZmljYXRlYXV0aG9yaXR5LzAWBgNVHSUBAf8EDDAKBggrBgEFBQcDAzAdBgNVHQ4EFgQUW3kEAgAGi7L0ksZGGodo6W8rjLUwDgYDVR0PAQH/BAQDAgeAMBMGCiqGSIb3Y2QGAQQBAf8EAgUAMA0GCSqGSIb3DQEBCwUAA4IBAQC6EFx0EMxOlZ38MZPNvNA8SLZvq2eWUIKtAFag4UyaSPIGCMYSYyW9FFP3Bh5guDbzoozvFgCGiumpSy5T1jLT4SaZ9UrS8+P3ODKmanQLEGyL7s3n+5fFKpR5tsM58Nh9zEpYNO/X8lyhG5y9FWObs5N+OdQMETGBDvdpSgZsKJhwnZoImk39gLL9QWK3yvXYOgn6eHi0iF2tsRC8J87X9d9qRCCidnUH4s1+3jnu5n3ug9rnn4aatLhy7F08m4DuLJ+UIAUNcQKQEAeMJOFj1az5aNRZ7P4fmOwBq0SSFlT0O5X+DnHZ6pCcWg3DX+roObyAZtcGrr5O8x1RS4L3MYID3jCCA9oCAQEwgYkwdTFEMEIGA1UEAww7QXBwbGUgV29ybGR3aWRlIERldmVsb3BlciBSZWxhdGlvbnMgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkxCzAJBgNVBAsMAkczMRMwEQYDVQQKDApBcHBsZSBJbmMuMQswCQYDVQQGEwJVUwIQKuZDboCQ5CNDRCgXSbguRDANBglghkgBZQMEAgEFAKCCAiUwGAYJKoZIhvcNAQkDMQsGCSqGSIb3DQEHATAcBgkqhkiG9w0BCQUxDxcNMjEwNTEyMTMzOTE1WjAvBgkqhkiG9w0BCQQxIgQgDgoyEjeS5nAaLKPP1ipwUJZMzIE2bQo3c8NhXnhXsvowWwYJKoZIhvdjZAkCMU4wHQYFKw4DAhoEFP1ZZFGydVZolRxPunKoC23Eul91MC0GCWCGSAFlAwQCAQQgUv3dyfq5V+AU0fb3YOqzHalWU+mJYU39xh4oUft6H+swggFbBgkqhkiG92NkCQExggFMBIIBSDw/eG1sIHZlcnNpb249IjEuMCIgZW5jb2Rpbmc9IlVURi04Ij8+CjwhRE9DVFlQRSBwbGlzdCBQVUJMSUMgIi0vL0FwcGxlLy9EVEQgUExJU1QgMS4wLy9FTiIgImh0dHA6Ly93d3cuYXBwbGUuY29tL0RURHMvUHJvcGVydHlMaXN0LTEuMC5kdGQiPgo8cGxpc3QgdmVyc2lvbj0iMS4wIj4KPGRpY3Q+Cgk8a2V5PmNkaGFzaGVzPC9rZXk+Cgk8YXJyYXk+CgkJPGRhdGE+CgkJL1Zsa1ViSjFWbWlWSEUrNmNxZ0xiY1M2WDNVPQoJCTwvZGF0YT4KCQk8ZGF0YT4KCQlVdjNkeWZxNVYrQVUwZmIzWU9xekhhbFdVK2s9CgkJPC9kYXRhPgoJPC9hcnJheT4KPC9kaWN0Pgo8L3BsaXN0PgowDQYJKoZIhvcNAQEBBQAEggEAanddMnPtmVSxg1z3/RpdT6PlJwcwH7G0KODwM8P8njjwKPuEHmn5JvRnkr0yWiwOkYESZhNAg7Z5onQXXA83xA6IMGcZb8i9cCBcnsXCIF2GO1LlpcfnBZVjaULfWRMkjp41UO+KsMsoRrGhSo6JDDSHcLxEQ6xTXP6hq5Fe+Wu7TUZu+Ofp3xskknQFjABZZgaVfgjFWaLgFkScvAXyKN1IX1jTnWVjVHv03pyp5tLWh1Cp6MeVGY3zt+IH3vxKr1xo2CoM09kc1QgaVZZ+wzYmcY04yWhSdJeb/T/eoZysvm897ALwtOgn+EZsa1twbd4NLb28KVLj8YACXmgHdgAAAAAAAA=="; sysctl 获取的设备信息:机型、内存数据等 1056 = "iPhone9%2c2,D11AP,iPhone9%2c2,D11AP,nil,2,65536,65536,3145728,nil,0x0100000C,1,nil,nil,1234,3146072064,3146072064,2813394944"; 1003 = "1621311387.431723"; // boot_time sysctl获取 KERN_BOOTTIME = 21 |0x15 1009 = "en0:172.24.106.120,en2:169.254.132.16"; // IP 1015 = ""; 1021 = "14.1"; // 系统版本 systemVersion 1027 = "me.sensheng.rayful2.TestFP"; // identifier //一些路径的 stat信息: 三个时间 、 ino st_dev 文件大小 1033 = "/var/containers:16777224:45:1621321250.950846:1621321251.024679:1587882316.649082:160,/var/mobile/Containers/Data:16777224:16666:1587882365.489126:1587882365.489126:1587882365.488196:256,/Applications:16777218:23:1617087892.705233:1617087892.705233:1600665379.020372:3456,/var/containers/Bundle/Application:16777224:16675:1621319658.857959:1621319658.857959:1587882365.489236:3264,/System/Library/Caches/com.apple.dyld/dyld_shared_cache_arm64:16777218:240894:1600665458:1604321637.973765:1600665458:2071494656,/System/Library/CoreServices:16777218:87411:1604321864.71446:1604321864.71446:1600665465.54423:1184,/var/mobile/Containers/Data/Application/47E75209-64AF-4F43-AE14-204D57BDF53C/Documents:16777224:39377285:1621311608.182579:1621311608.195006:1621311608.182579:64,TestFP:16777224:39377242:1620826754:1621311608.183973:1620826754:777408,/usr/lib/Cephei.framework/Cephei:16777218:395692:1599985175:1605508819.64767:1605508819:296656,/usr/lib/CepheiUI.framework/CepheiUI:16777218:395695:1599985177:1605508819.64777:1605508819:254672,/usr/lib/libexpat.1.dylib:16777218:584232:1535512546:1616834683.579731:1616834683:182880,/usr/lib/libobjc-trampolines.dylib:16777218:357531:1604322026.926359:1604322026.926364:1600665645:50048,/usr/lib/librocketbootstrap.dylib:16777218:382357:1601239990:1604637230.74314:1604637230:323504"; 1051 = 0; 1057 = "Darwin,20.0.0,nil,18A8395,D2D621E1F09632499EBBC19AEC5757F9B5CE8ED1B02AE098D767244A82EA6F54,0"; // sysctl内核信息 HW_MACHINE 计算 sha256 1004 = "1621341841.911988"; // current_time 当前时间 1010 = "pdp_ip0:10.40.212.11"; cip ,运营商网络ip 1016 = 1; 1022 = guohao; 1028 = "zh-Hans-CN"; 1034 = "B7F14752-B349-49FD-9910-630268ACAEFE"; // uuid keychain idfa NSUUID 1046 = "<?xml version=\"1.0\" encoding=\"UTF-8\"?>\n<!DOCTYPE plist PUBLIC \"-//Apple//DTD PLIST 1.0//EN\" \"http://www.apple.com/DTDs/PropertyList-1.0.dtd\">\n<plist version=\"1.0\">\n<dict>\n\t<key>application-identifier</key>\n\t<string>HKB8WPFBR9.</string>\n\t<key>com.apple.developer.default-data-protection</key>\n\t<string>NSFileProtectionComplete</string>\n\t<key>com.apple.developer.team-identifier</key>\n\t<string>HKB8WPFBR9</string>\n\t<key>get-task-allow</key>\n\t<false/>\n\t<key>inter-app-audio</key>\n\t<true/>\n\t<key>keychain-access-groups</key>\n\t<array>\n\t\t<string>HKB8WPFBR9.com.centauri.wsj.keystoregroup</string>\n\t\t<string>HKB8WPFBR9.com.stove.globaldata</string>\n\t\t<string>HKB8WPFBR9.com.tencent.wsj.keystoregroup</string>\n\t\t<string>HKB8WPFBR9.</string>\n\t</array>\n</dict>\n</plist>\n"; 1052 = "/Library/MobileSubstrate/DynamicLibraries/FlexList.dylib,/Library/MobileSubstrate/DynamicLibraries/HideJB.dylib,/Library/MobileSubstrate/DynamicLibraries/antiplugin.dylib,/Library/MobileSubstrate/DynamicLibraries/zorro.dylib,/Library/MobileSubstrate/DynamicLibraries/zzzzzLiberty.dylib,/usr/lib/Cephei.framework/Cephei,/usr/lib/CepheiUI.framework/CepheiUI,/usr/lib/libexpat.1.dylib,/usr/lib/libobjc-trampolines.dylib,/usr/lib/librocketbootstrap.dylib,/usr/lib/libsubstitute.0.dylib,/usr/lib/libsubstrate.dylib,/usr/lib/substitute-inserter.dylib,/usr/lib/substitute-loader.dylib"; 200 = ""; 1005 = 37494878208; // 文件系统大小 1011 = ""; 1017 = "172.24.67.27:8080"; proxy 代理 1023 = "\U4e2d\U56fd\U8054\U901a"; // 运营商名: 中国联通 1035 = ""; 1047 = 9A00886F806EDB778DE01846DD2478A6; cms md5 1059 = ""; }设备ID可能相关字段:
1001 –> IDFA
1002-> IDFV
1007->内存大小
1008 -> 屏幕亮度
1020 -> 设备型号
1056 -> sysctl 获取的设备硬件信息
1057 -> 几个内核信息
1003 -> 上次系统启动时间
1021 -> 系统版本
1033 -> 文件系统 stat信息:读写和篡改时间 ino 大小 st_dev
1010 -> 运营商网络IP
1022 -> 系统名
1034 -> keychain uuid
1005 -> 文件系统大小
1023 -> 运营商名称
真机测试:
1、同一个设备清空keychain和app缓存前后,设备ID相同
2、同一个设备不同APP获取设备ID相同
3、同一个设备 HOOK stat函数,篡改函数的返回值,设备ID不同

风险识别相关字段:
1019 –> 越狱状态值
1044—> 签名段二进制数据
1033- 文件系统stat信息
1046 –> entitlement信息
1052 –-> 动态库注入
1017 –> 代理信息
1051 -->调试
1)越狱检测:
a、检测文件路径:
/private/var/lib/apt/
/Applications/Cydia.app
/Library/MobileSubstrate/MobileSubstrate.dylib
/etc/apt
/Applications/Sileo.app
/usr/lib/libsubstrate.dylib
/usr/lib/substitute-inserter.dylib
/usr/lib/libsubstitute.dylib
/usr/bin/ssh
b、检测是否可以打开URL:
cydia://
sileo://
c、检测符号链接:
/Applications
2)签名检测:
上报整个CMS签名段的二进制数据base64后的字符串
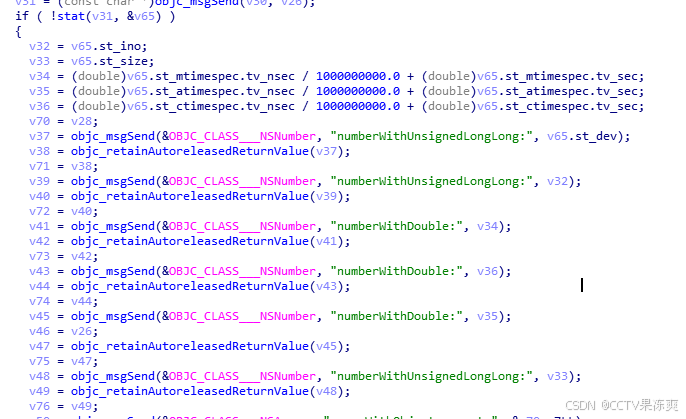
3)文件系统stat信息:
检测如下文件的stat信息(访问和修改等时间、ino值、dev值、文件大小):
/var/containers
/var/mobile/Containers/Data
/Applications
/var/containers/Bundle/Application
/System/Library/Caches/com.apple.dyld/dyld_shared_cache_arm64
/System/Library/CoreServices
/var/mobile/Containers/Data/Application/47E75209-64AF-4F43-AE14-204D57BDF53C/Documents(APP文档目录)
TestFP(APP主文件)
/usr/lib/Cephei.framework/Cephei(非法模块)
/usr/lib/CepheiUI.framework/CepheiUI(非法模块)
/usr/lib/libexpat.1.dylib
/usr/lib/libobjc-trampolines.dylib
/usr/lib/librocketbootstrap.dylib(非法模块)
Stat信息中的时间信息只有越狱状态下才能获取,即越狱设备可以根据stat时间信息计算设备ID
4)entitlement信息
包含APP一些信息,可识别重打包
5)动态库注入
task_info获取所有模块,NSFileTypeSymbolicLink判断注入的恶意动态库
6)代理检测
CFNetworkCopySystemProxySettings 检测
7)调试检测
Isatty & ioctl & getppid
8)自动化测试工具检测
检测web 8100端口:基于webagent的自动化测试工具