阅读量:0
文章目录
前言
处理新发布的CVE-2024-6387关于openssh的漏洞,升级openssh到9.8版本。
一、升级准备?
确认系统版本
[root@CentOS7 ~]# uname -a Linux CentOS7 3.10.0-1160.el7.x86_64 #1 SMP Mon Oct 19 16:18:59 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux [root@CentOS7 ~]# cat /etc/centos-release CentOS Linux release 7.9.2009 (Core) [root@CentOS7 ~]# ssh -V OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017 备份配置文件
cp -rf /etc/ssh /etc/ssh.bak cp -rf /usr/bin/openssl /usr/bin/openssl.bak cp -rf /etc/pam.d /etc/pam.d.bak cp -rf /usr/lib/systemd/system /usr/lib/systemd/system.bak 安装编译依赖工具包
这里要更换阿里的yum源,否则gcc升级不了版本,后边编译会失败
yum install -y vim gcc gcc-c++ glibc make autoconf openssl openssl-devel pcre-devel pam-devel zlib-devel tcp_wrappers-devel tcp_wrappers libedit-devel perl-IPC-Cmd wget tar lrzsz1 下载升级,依赖包
cd /usr/local/src wget https://www.zlib.net/zlib-1.3.1.tar.gz wget https://www.openssl.org/source/openssl-3.2.1.tar.gz wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.8p1.tar.gz tar -zxvf zlib-1.3.1.tar.gz tar -zxvf openssl-3.2.1.tar.gz tar -zxvf openssh-9.8p1.tar.gz 二、使用步骤
编译升级zlib
cd zlib-1.3.1 ls /usr/local/ ./configure --prefix=/usr/local/zlib make -j 2 make test make install ls /usr/local/zlib/ echo '/usr/local/zlib/lib' >> /etc/ld.so.conf.d/zlib.conf ldconfig -v 编译升级openssl
cd openssl-3.2.1 ls /usr/local/ ./config --prefix=/usr/local/openssl make -j2 make install mv /usr/bin/openssl /usr/bin/openssl.bak ll /usr/bin/open* ln -s /usr/local/openssl/bin/openssl /usr/bin/openssl ln -s /usr/local/openssl/lib64/libssl.so.3 /usr/lib64/libssl.so.3 ln -s /usr/local/openssl/lib64/libcrypto.so.3 /usr/lib64/libcrypto.so.3 echo '/usr/local/openssl/lib64' >> /etc/ld.so.conf.d/ssl.conf 确认openssl版本
[root@CentOS7 openssl-3.2.1]# openssl version -v OpenSSL 3.2.1 30 Jan 2024 (Library: OpenSSL 3.2.1 30 Jan 2024) [root@CentOS7 openssl-3.2.1]# openssl version -a OpenSSL 3.2.1 30 Jan 2024 (Library: OpenSSL 3.2.1 30 Jan 2024) built on: Mon May 20 03:16:20 2024 UTC platform: linux-x86_64 options: bn(64,64) compiler: gcc -fPIC -pthread -m64 -Wa,--noexecstack -Wall -O3 -DOPENSSL_USE_NODELETE -DL_ENDIAN -DOPENSSL_PIC -DOPENSSL_BUILDING_OPENSSL -DNDEBUG OPENSSLDIR: "/usr/local/openssl/ssl" ENGINESDIR: "/usr/local/openssl/lib64/engines-3" MODULESDIR: "/usr/local/openssl/lib64/ossl-modules" Seeding source: os-specific CPUINFO: OPENSSL_ia32cap=0xfffa32034f8bffff:0x18405fdef1bf27eb 卸载旧的sshd服务(切记不能关掉或重启远程工具)
[root@CentOS7 openssl-3.2.1]# yum remove openssh Loaded plugins: fastestmirror Resolving Dependencies --> Running transaction check ---> Package openssh.x86_64 0:7.4p1-21.el7 will be erased --> Processing Dependency: openssh = 7.4p1-21.el7 for package: openssh-clients-7.4p1-21.el7.x86_64 --> Processing Dependency: openssh = 7.4p1-21.el7 for package: openssh-server-7.4p1-21.el7.x86_64 --> Running transaction check ---> Package openssh-clients.x86_64 0:7.4p1-21.el7 will be erased ---> Package openssh-server.x86_64 0:7.4p1-21.el7 will be erased --> Finished Dependency Resolution Dependencies Resolved ================================================================================================================ Package Arch Version ================================================================================================================ Removing: openssh x86_64 7.4p1-21.el7 Removing for dependencies: openssh-clients x86_64 7.4p1-21.el7 openssh-server x86_64 7.4p1-21.el7 Transaction Summary ================================================================================================================ Remove 1 Package (+2 Dependent packages) Installed size: 5.4 M Is this ok [y/N]: y Downloading packages: Running transaction check Running transaction test Transaction test succeeded Running transaction Erasing :openssh-server-7.4p1-21.el7.x86_64 Erasing :openssh-clients-7.4p1-21.el7.x86_64 Erasing :openssh-7.4p1-21.el7.x86_64 Verifying :openssh-clients-7.4p1-21.el7.x86_64 Verifying :openssh-7.4p1-21.el7.x86_64 Verifying :openssh-server-7.4p1-21.el7.x86_64 Removed: openssh.x86_64 0:7.4p1-21.el7 Dependency Removed: openssh-clients.x86_64 0:7.4p1-21.el7 openssh-server.x86_64 0:7. Complete! [root@CentOS7 openssl-3.2.1]# rm -rf /etc/ssh/* 编译升级openssh
cd openssh-9.8p1 ls ./configure --prefix=/usr/local/openssh --sysconfdir=/etc/ssh --with-pam --with-ssl-dir=/usr/local/openssl/ --with-zlib=/usr/local/zlib 确认PAM编译成功
OpenSSH has been configured with the following options: User binaries: /usr/local/openssh/bin System binaries: /usr/local/openssh/sbin Configuration files: /etc/ssh Askpass program: /usr/local/openssh/libexec/ssh-askpass Manual pages: /usr/local/openssh/share/man/manX PID file: /var/run Privilege separation chroot path: /var/empty sshd default user PATH: /usr/bin:/bin:/usr/sbin:/sbin:/usr/local/openssh/bin Manpage format: doc PAM support: yes OSF SIA support: no KerberosV support: no SELinux support: no libedit support: no libldns support: no Solaris process contract support: no Solaris project support: no Solaris privilege support: no IP address in $DISPLAY hack: no Translate v4 in v6 hack: yes BSD Auth support: no Random number source: OpenSSL internal ONLY Privsep sandbox style: seccomp_filter PKCS#11 support: yes U2F/FIDO support: yes Host: x86_64-pc-linux-gnu Compiler: cc -std=gnu11 Compiler flags: -g -O2 -pipe -Wall -Wextra -Wpointer-arith -Wuninitialized -Wsign-compare -Wformat-security -Wsizeof-pointer-memaccess -Wno-pointer-sign -Wno-unused-parameter -Wno-unused-result -fno-strict-aliasing -D_FORTIFY_SOURCE=2 -ftrapv -fno-builtin-memset -fstack-protector-strong -fPIE Preprocessor flags: -I/usr/local/openssl//include -I/usr/local/zlib/include -D_XOPEN_SOURCE=600 -D_BSD_SOURCE -D_DEFAULT_SOURCE -D_GNU_SOURCE -DOPENSSL_API_COMPAT=0x10100000L Linker flags: -L/usr/local/openssl//lib64 -L/usr/local/zlib/lib -Wl,-z,relro -Wl,-z,now -Wl,-z,noexecstack -fstack-protector-strong -pie Libraries: -ldl -lutil -lresolv +for channels: -lcrypto -lz +for sshd: -lcrypt -lpam PAM is enabled. You may need to install a PAM control file for sshd, otherwise password authentication may fail. Example PAM control files can be found in the contrib/ subdirectory make -j 2 make install 配置sshd服务
cp contrib/redhat/sshd.init /etc/init.d/sshd cp /etc/pam.d/sshd /etc/pam.d/sshd.bak cp /usr/local/openssh/sbin/sshd /usr/sbin/ cp /usr/local/openssh/bin/ssh /usr/bin/ cp /usr/local/openssh/bin/ssh-keygen /usr/bin/ ll /etc/init.d/ chkconfig --add sshd echo 'PermitRootLogin yes' >> /etc/ssh/sshd_config echo 'PasswordAuthentication yes' >> /etc/ssh/sshd_config echo 'UsePAM yes' >> /etc/ssh/sshd_config 配置PAM模块
cat /etc/pam.d/sshd #把下面内容复制进去 #%PAM-1.0 auth required pam_sepermit.so auth substack password-auth auth include postlogin # Used with polkit to reauthorize users in remote sessions -auth optional pam_reauthorize.so prepare account required pam_nologin.so account include password-auth password include password-auth # pam_selinux.so close should be the first session rule session required pam_selinux.so close session required pam_loginuid.so # pam_selinux.so open should only be followed by sessions to be executed in the user context session required pam_selinux.so open env_params session required pam_namespace.so session optional pam_keyinit.so force revoke session include password-auth session include postlogin # Used with polkit to reauthorize users in remote sessions -session optional pam_reauthorize.so prepare 启动ssh /etc/init.d/sshd restart 登录验证
[root@CentOS7 ~]# sshd -V OpenSSH_9.8p1, OpenSSL 3.2.1 30 Jan 2024 [root@CentOS7 ~]# ssh -V OpenSSH_9.8p1, OpenSSL 3.2.1 30 Jan 2024 [root@CentOS7 ~]# [root@CentOS7 ~]# systemctl status sshd ● sshd.service - SYSV: OpenSSH server daemon Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled) Active: active (running) since Mon 2024-05-20 11:58:59 CST; 12min ago Docs: man:systemd-sysv-generator(8) Process: 54017 ExecStop=/etc/rc.d/init.d/sshd stop (code=exited, status=0/SUCCESS) Process: 54024 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS) Main PID: 54032 (sshd) CGroup: /system.slice/sshd.service ├─40735 sshd: root@pts/1 ├─40737 sshd: root@notty ├─40739 -bash ├─40756 /usr/local/openssh/libexec/sftp-server └─54032 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startup May 20 11:58:59 CentOS7 systemd[1]: Starting SYSV: OpenSSH server daemon... May 20 11:58:59 CentOS7 sshd[54032]: Server listening on 0.0.0.0 port 22. May 20 11:58:59 CentOS7 sshd[54032]: Server listening on :: port 22. May 20 11:58:59 CentOS7 sshd[54024]: Starting sshd:[ OK ] May 20 11:58:59 CentOS7 systemd[1]: Started SYSV: OpenSSH server daemon. May 20 11:59:17 CentOS7 sshd[54037]: Accepted keyboard-interactive/pam for root from 192.168.14.1 port 53027 ssh2 May 20 11:59:17 CentOS7 sshd[54040]: Accepted password for root from 192.168.14.1 port 53031 ssh2 问题
问题:
1.升级完之后无法登录(需要手动更改)
echo ‘PermitRootLogin yes’ >> /etc/ssh/sshd_config
echo ‘PasswordAuthentication yes’ >> /etc/ssh/sshd_config
echo ‘UsePAM yes’ >> /etc/ssh/sshd_config
2.ssh无法启动提示(sshd: no hostkeys available – exiting)需要修改ssh权限
chown root:root /etc/ssh/*
chmod 600 /etc/ssh/*
3.启动后无法登录
关闭SElinux不重启系统的方法:
修改**/etc/sysconfig/selinux**文件(虚拟机用的是CentOS 7)
vi /etc/sysconfig/selinux
将 **#SELINUX=**enforcing 改为 **SELINUX=**disabled
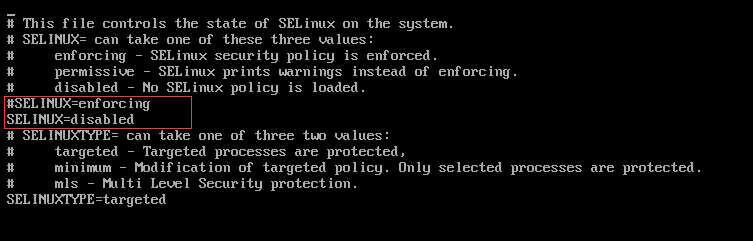
命令重启后生效,如果不想重启,用命令
setenforce 0
