阅读量:0
Jumpserver在线安装及部署认证服务器CA
| 主机 | IP | 功能 |
|---|---|---|
| JumpServer | 192.168.1.34 | 堡垒机管理资产及权限 |
| CA认证服务器 | 192.168.1.37 | 提供HTTPS安全加密 |
堡垒机一键在线安装
##z在线安装 curl -sSL https://resource.fit2cloud.com/jumpserver/jumpserver/releases/latest/download/quick_start.sh | bash 注意事项
##默认密码 admin/admin ##启动JumpServer 首先进入/opt/jumpserver-installer-v3.9.3/ 执行 ./jmsctl.sh start ##关闭JumpServer 首先进入/opt/jumpserver-installer-v3.9.3/ 执行 ./jmsctl.sh stop ##需要使用HTTPS服务 将文件证书放在/opt/jumpserver/config/nginx/cert路径下 修改配置文件 vi /opt/jumpserver/config/config.txt SSL_CERTIFICATE=/opt/jumpserver/config/nginx/cert/httpd.crt SSL_CERTIFICATE_KEY=/opt/jumpserver/config/nginx/cert/httpd.key ps:注意,需要先停止JumpServer服务后再修改配置文件 ##关闭setenforce setenforce 0 部署CA服务器
###简历CA服务器 ##生成密钥 [root@localhost ~]# (umask 007; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) ps: ():表示此命令在子进程中运行,其目的是为了不改变当前Shell中的umask值; genrsa:生成私钥; -out:私钥的存放路径,cakey.pem:为密钥名,与配置文件中保持一致; 2048:密钥长度,默认为1024 ##自签证书 [root@localhost ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 1000 ps: req:生成证书签署请求; -x509:生成自签署证书; -days n:证书的有效天数; -new:新请求; -key /path/to/keyfile:指定私钥文件; -out /path/to/somefile:输出文件位置 ##初始化工作环境 [root@localhost ~]# touch /etc/pki/CA/{index.txt,serial} [root@localhost ~]# echo 01 > /etc/pki/CA/serial ps: index.txt:索引文件,用于匹配证书编号; serial:证书序列号文件,只在首次生成证书时赋值 实例:堡垒机HTTPS安全加密
登录堡垒机
##生成密钥对 [root@localhost ~]# mkdir -p /etc/httpd/ssl [root@localhost ~]# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048) ##生成证书信息 [root@localhost ~]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]:CN State or Province Name (full name) [JS]:JS Locality Name (eg, city) [SZ]:SZ Organization Name (eg, company) [JFHY]:JHFY Organizational Unit Name (eg, section) [JFHY]:JFHY Common Name (eg, your name or your server's hostname) [jfhy.com]:jfhy.com Email Address [www]:www Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:123456 An optional company name []:www ##将刚刚申请的请求文件发送给CA服务器 [root@localhost ~]# scp /etc/httpd/ssl/httpd.csr root@192.168.1.37:/etc/pki/CA/crl 登录CA服务器
##签署证书 [root@localhost ~]# openssl ca -in /etc/pki/CA/crl/httpd.csr -out /etc/pki/CA/crl/httpd.crt -days 1000 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok The organizationName field needed to be the same in the CA certificate (JFHY) and the request (JHFY) ##将签名好的证书发送给堡垒机 [root@localhost ~]# scp httpd.crt root@192.168.1.34:/etc/httpd/ssl 吊销证书
登录CA服务器
##获取证书serial [root@localhost ~]# openssl x509 -in httpd.crt -noout -serial -subject ps: x509:证书格式; -in:要吊销的证书; -noout:不输出额外信息; -serial:显示序列号; -subject:显示subject信息 ##CA验证信息 [root@localhost ~]# cd /etc/pki/CA/ [root@localhost CA]# cat index.txt ##吊销证书 [root@localhost CA]# openssl ca -revoke /etc/pki/CA/newcerts/01.pem ##删除证书 查看被吊销的证书列表 [root@localhost CA]# cat /etc/pki/CA/index.txt 生成吊销证书的编号(如果是第一次吊销) [root@localhost CA]# echo 00 > /etc/pki/CA/crlnumber 更新证书吊销列表 [root@localhost CA]# cd crl [root@localhost CA]# openssl ca -gencrl -out ca.crl ps: -gencrl:生成证书吊销列表 错误
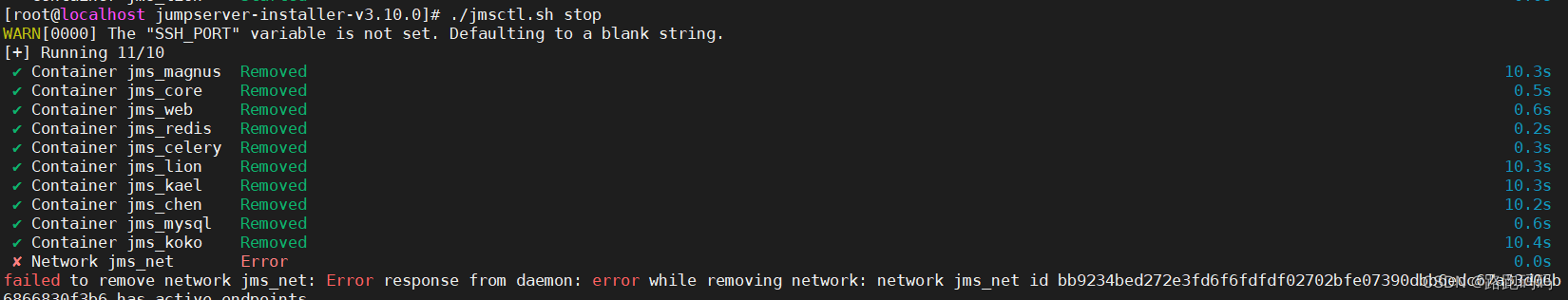
如出现以上错误,需要在配置文件中修改https默认443端口 自定义端口 如23443
放通防火墙
firewall-cmd --per --add-port=23443/tcp
firewall-cmd --reload
注意
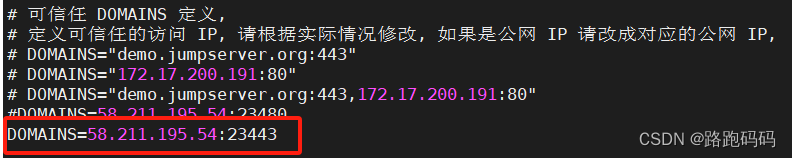
如果修改了端口,需要在配置文件中修改一下:
-1714440104784)]
如出现以上错误,需要在配置文件中修改https默认443端口 自定义端口 如23443
放通防火墙
firewall-cmd --per --add-port=23443/tcp
firewall-cmd --reload
注意
如果修改了端口,需要在配置文件中修改一下: