先自我介绍一下,小编浙江大学毕业,去过华为、字节跳动等大厂,目前阿里P7
深知大多数程序员,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年最新网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。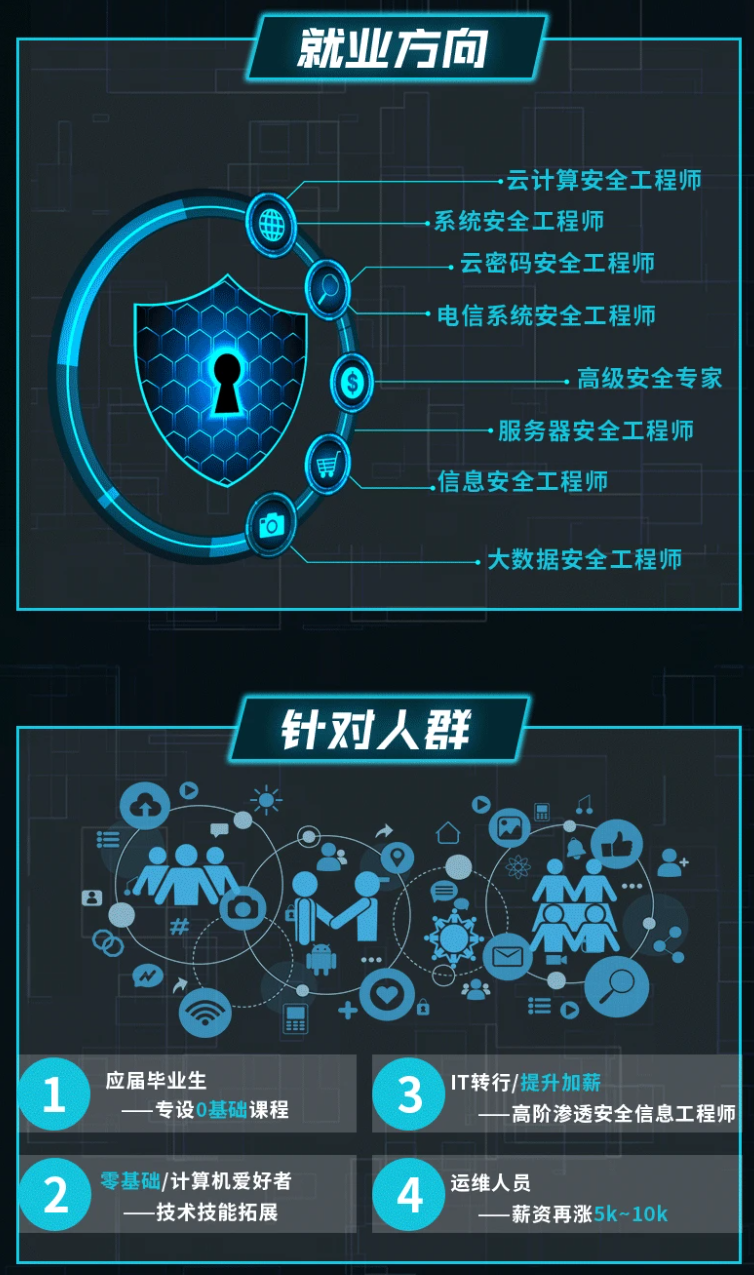
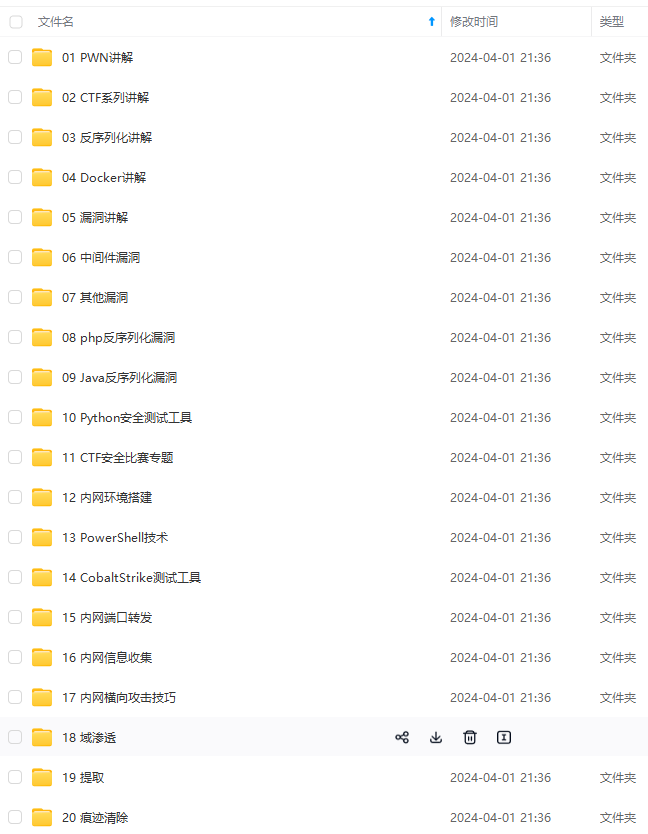
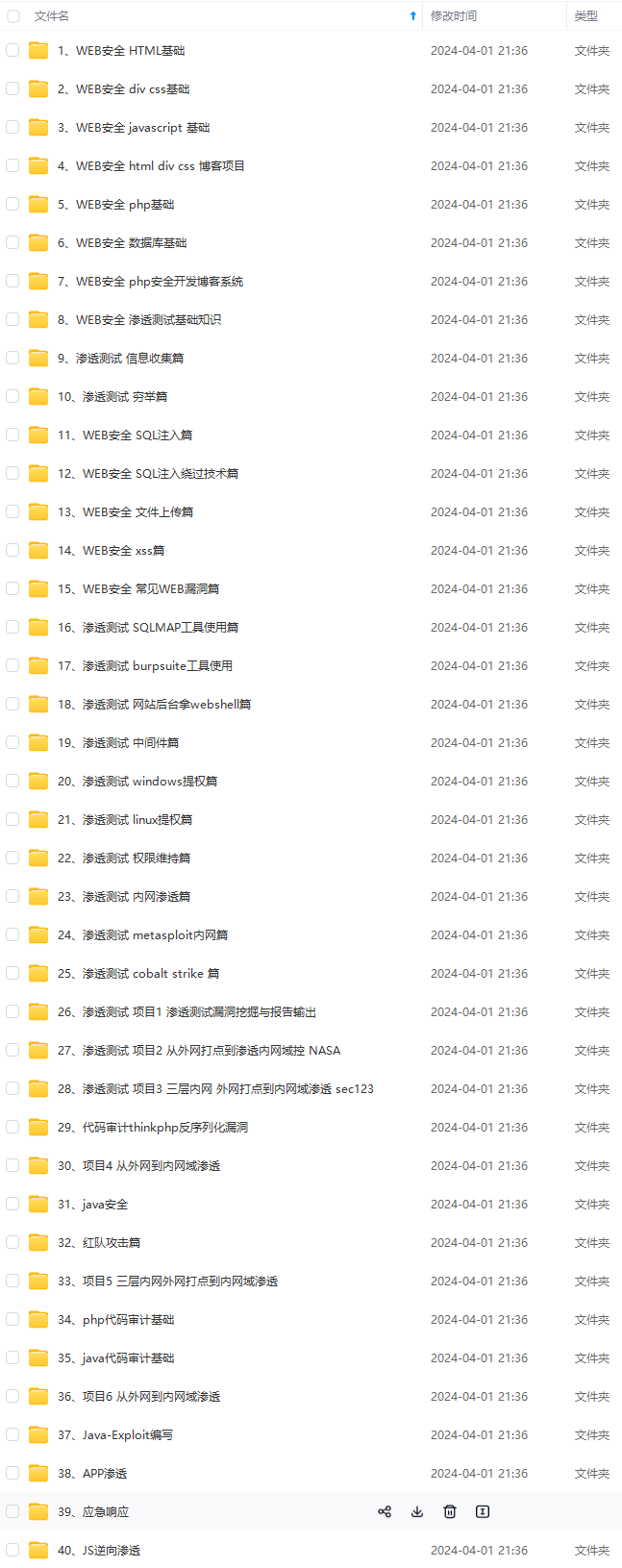
既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较多,这里只是将部分目录截图出来,全套包含大厂面经、学习笔记、源码讲义、实战项目、大纲路线、讲解视频,并且后续会持续更新
如果你需要这些资料,可以添加V获取:vip204888 (备注网络安全)
正文
sed -i 's/#PASS\_MAX\_DAYS/PASS\_MAX\_DAYS/' /etc/login.defs PASS\_MAX\_DAYS=`cat /etc/login.defs | grep PASS\_MAX\_DAYS | grep -v ^# | awk '{print $2}'` fi if [ -z $PASS\_MAX\_DAYS ];then echo "............[N] Password Validity Period: Reset failed" elif [ $PASS\_MAX\_DAYS -le 90 -a $PASS\_MAX\_DAYS -ge 30 ];then echo "......[Y] Password Validity Period: $PASS\_MAX\_DAYS days" else sed -i '/PASS\_MAX\_DAYS/s/'"${PASS\_MAX\_DAYS}"'/90/g' /etc/login.defs PASS_MAX_DAYS=cat /etc/login.defs | grep PASS\_MAX\_DAYS | grep -v ^# | awk '{print $2}'
if [ $PASS_MAX_DAYS -le 90 -a $PASS_MAX_DAYS -ge 30 ];then
echo “…[Y] Password Validity Period: $PASS_MAX_DAYS days”
else
echo “…[N] Password Validity Period: Reset failed”
fi
fi
}
#检查日志保留时间
function CheckLogBackupTime() {
Log_Backup_Time=cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'
if [ -z $Log_Backup_Time ];then
sed -i ‘s/#rotate/rotate/’ /etc/logrotate.conf
Log_Backup_Time=cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'
fi
if [ -z $Log_Backup_Time ];then
echo “…[N] Log backup Time,Configuration does not exist”
elif [ $Log_Backup_Time -ge 26 ];then
echo “…[Y] Log backup Time: L o g _ B a c k u p _ T i m e w e e k s " e l s e s e d − i ′ / r o t a t e / s / ′ " Log\_Backup\_Time weeks" else sed -i '/rotate/s/'" Log_Backup_Timeweeks"elsesed−i′/rotate/s/′"{Log_Backup_Time}”‘/26/g’ /etc/logrotate.conf
Log_Backup_Time=cat /etc/logrotate.conf |head -n 10|grep "rotate "| grep -v ^# | head -n 1|awk '{print $2}'
if [ $Log_Backup_Time -ge 26 ];then
echo “…[Y] Log backup Time: $Log_Backup_Time weeks”
else
echo “…[N] Log backup Time,Reset failed”
fi
fi
}
#检查会话超时时间
function CheckConnectionTimeout() {
Connection_Timeout=cat /etc/profile | grep 'export TMOUT' | grep -v ^# | cut -d= -f2
if [ -z C o n n e c t i o n _ T i m e o u t ] ; t h e n s e d − i ′ Connection\_Timeout ];then sed -i ' Connection_Timeout];thensed−i′a export TMOUT=1800’ /etc/profile
elif [ $Connection_Timeout -gt 1800 -o C o n n e c t i o n _ T i m e o u t − l t 600 ] ; t h e n s e d − i ′ / T M O U T / s / ′ " Connection\_Timeout -lt 600 ];then sed -i '/TMOUT/s/'" Connection_Timeout−lt600];thensed−i′/TMOUT/s/′"{Connection_Timeout}"‘/1800/g’ /etc/profile
fi
source /etc/profile
Connection_Timeout=cat /etc/profile | grep 'export TMOUT' | grep -v ^# | cut -d= -f2
if [ $Connection_Timeout -le 1800 -a $Connection_Timeout -ge 600 ];then
echo “…[Y] Connection timeout: $Connection_Timeout seconds”
else
echo “…[N] Connection timeout: Reset failed”
fi
}
#检查共享账户
function CheckSharedUser() {
usermod -L shutdown 2>/dev/null
usermod -L halt 2>/dev/null
echo “…[Y] Shared user: Locked”
}
#检查审计策略
function CheckAuditLogs() {
Audit_Logs=auditctl -s | grep enabled | awk '{print $2}'
if [ $Audit_Logs -ne 1 ];then
systemctl start auditd
systemctl enable auditd
fi
Audit_Logs=auditctl -s | grep enabled | awk '{print $2}'
if [ $Audit_Logs -eq 1 ];then
echo “…[Y] Audit Policy: $Audit_Logs Enable”
else
echo “…[N] Audit Policy: $Audit_Logs Disabled”
fi
}
#检查分权账户
function CheckAuthorizedUser() {
shenji=cat /etc/passwd |grep shenji | grep -v ^# | cut -d: -f 1
anquan=cat /etc/passwd |grep anquan | grep -v ^# | cut -d: -f 1
sysadmin=cat /etc/passwd |grep sysadmin | grep -v ^# | cut -d: -f 1
if [ -z KaTeX parse error: Expected 'EOF', got '#' at position 51: … shenji:In123!@#̲123|chpasswd s…a shenji ALL = (root) NOPASSWD: /usr/bin/cat , /usr/bin/less , /usr/bin/more , /usr/bin/tail , /usr/bin/head’ /etc/sudoers
fi
if [ -z $anquan ];then
useradd anquan
echo anquan:In123!@#123|chpasswd
fi
if [ -z $sysadmin ];then
useradd sysadmin
echo sysadmin:In123!@#123|chpasswd
fi
shenji=cat /etc/passwd |grep shenji | grep -v ^# | cut -d: -f 1
anquan=cat /etc/passwd |grep anquan | grep -v ^# | cut -d: -f 1
sysadmin=cat /etc/passwd |grep sysadmin | grep -v ^# | cut -d: -f 1
if [ -z $shenji -o -z $anquan -o -z $sysadmin ];then
echo “…[N] Authorized user: $shenji, $anquan, $sysadmin”
else
echo “…[Y] Authorized user: $shenji, $anquan, $sysadmin”
fi
}
#检查登录失败锁定配置CentOS
function CheckLoginFailureLock_CentOS() {
Login_Failure_Lock=grep "pam\_tally2.so" /etc/pam.d/system-auth| grep -v ^#|head -n 1|awk '{print $7}'
if [ -z $Login_Failure_Lock ];then
sed -i ‘/pam_tally2.so/s/#auth/auth/g’ /etc/pam.d/system-auth
Login_Failure_Lock=grep "pam\_tally2.so" /etc/pam.d/system-auth| grep -v ^#|head -n 1|awk '{print $7}'
fi
if [ -z L o g i n _ F a i l u r e _ L o c k ] ; t h e n s e d − i ′ Login\_Failure\_Lock ];then sed -i ' Login_Failure_Lock];thensed−i′a auth required pam_tally2.so onerr=fail audit silent dent=5 unlock_time=600 even_deny_root root_unlock_time=600’ /etc/pam.d/system-auth
else
Login_Failure_Lock=grep "pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600" /etc/pam.d/system-auth| grep -v ^#|awk '{print $7}'
if [ -z KaTeX parse error: Expected 'EOF', got '#' at position 63: …lly2.so/s/auth/#̲auth/g' /etc/pa…a auth required pam_tally2.so onerr=fail audit silent dent=5 unlock_time=600 even_deny_root root_unlock_time=600’ /etc/pam.d/system-auth
fi
fi
Login_Failure_Lock=grep "pam\_tally2.so onerr=fail audit silent dent=5 unlock\_time=600" /etc/pam.d/system-auth| grep -v ^#|awk '{print $7","$8","$10}'
if [ -z $Login_Failure_Lock ];then
echo “…[N] Login Failure Lock: Reset failed”
else
echo “…[Y] Login Failure Lock: $Login_Failure_Lock”
fi
}
#检查登录失败锁定配置SUSE
function CheckLoginFailureLock_SUSE() {
Login_Failure_Number=cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'
if [ -z $Login_Failure_Number ];then
sed -i ‘s/#LOGIN_RETRIES/LOGIN_RETRIES/’ /etc/login.defs
Login_Failure_Number=cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'
fi
if [ -z $Login_Failure_Number ];then
echo “…[N] Number of login failures: No configuration”
elif [ $Login_Failure_Number -le 8 -a $Login_Failure_Number -ge 3 ];then
echo “…[Y] Number of login failures: L o g i n _ F a i l u r e _ N u m b e r " e l s e s e d − i ′ / L O G I N _ R E T R I E S / s / ′ " Login\_Failure\_Number" else sed -i '/LOGIN\_RETRIES/s/'" Login_Failure_Number"elsesed−i′/LOGIN_RETRIES/s/′"{Login_Failure_Number}”‘/5/g’ /etc/login.defs
Login_Failure_Number=cat /etc/login.defs | grep LOGIN\_RETRIES | grep -v ^# | awk '{print $2}'
if [ $Login_Failure_Number -le 8 -a $Login_Failure_Number -ge 3 ];then
echo “…[Y] Number of login failures: $Login_Failure_Number”
else
echo “…[N] Number of login failures: No configuration”
fi
fi
Login_Failure_Time=cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'
if [ -z $Login_Failure_Time ];then
sed -i ‘s/#LOGIN_TIMEOUT/LOGIN_TIMEOUT/’ /etc/login.defs
Login_Failure_Time=cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'
fi
if [ -z $Login_Failure_Time ];then
echo “…[N] Login failure lock time: Reset failed”
elif [ $Login_Failure_Time -le 1800 -a $Login_Failure_Time -ge 300 ];then
echo “…[Y] Login failure lock time: L o g i n _ F a i l u r e _ T i m e s e c o n d s " e l s e s e d − i ′ / L O G I N _ T I M E O U T / s / ′ " Login\_Failure\_Time seconds" else sed -i '/LOGIN\_TIMEOUT/s/'" Login_Failure_Timeseconds"elsesed−i′/LOGIN_TIMEOUT/s/′"{Login_Failure_Time}”‘/300/g’ /etc/login.defs
Login_Failure_Time=cat /etc/login.defs | grep LOGIN\_TIMEOUT | grep -v ^# | awk '{print $2}'
if [ $Login_Failure_Time -le 1800 -a $Login_Failure_Time -ge 300 ];then
echo “…[Y] Login failure lock time: $Login_Failure_Time seconds”
else
echo “…[N] Login failure lock time: Reset failed”
fi
fi
}
#检查密码策略CentOS
function CheckPasswordPolicy_CentOS() {
Password_Policy=grep "pam\_cracklib.so" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'
if [ -z $Password_Policy ];then
sed -i ‘/pam_cracklib.so/s/#password/password/g’ /etc/pam.d/system-auth
Password_Policy=grep "pam\_cracklib.so" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'
fi
if [ -z P a s s w o r d _ P o l i c y ] ; t h e n s e d − i ′ Password\_Policy ];then sed -i ' Password_Policy];thensed−i′a password requisite pam_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1’ /etc/pam.d/system-auth
else
Password_Policy=grep "pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4}'
if [ -z KaTeX parse error: Expected 'EOF', got '#' at position 65: ….so/s/password/#̲password/g' /et…a password requisite pam_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1’ /etc/pam.d/system-auth
fi
fi
Password_Policy=grep "pam\_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/system-auth| grep -v ^#|awk '{print $4","$5","$6","$7","$8}'
if [ -z $Password_Policy ];then
echo “…[N] Password Policy: Reset failed”
else
echo “…[Y] Password Policy: $Password_Policy”
fi
}
#检查密码策略SUSE
function CheckPasswordPolicy_SUSE() {
Password_Policy=grep "pam\_cracklib.so" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'
if [ -z $Password_Policy ];then
sed -i ‘/pam_cracklib.so/s/#password/password/g’ /etc/pam.d/common-password
Password_Policy=grep "pam\_cracklib.so" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'
fi
if [ -z P a s s w o r d _ P o l i c y ] ; t h e n s e d − i ′ Password\_Policy ];then sed -i ' Password_Policy];thensed−i′a password requisite pam_cracklib.so retry=3 difok=3 minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1’ /etc/pam.d/common-password
else
Password_Policy=grep "minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/common-password| grep -v ^#|awk '{print $4}'
if [ -z KaTeX parse error: Expected 'EOF', got '#' at position 65: ….so/s/password/#̲password/g' /et…a password requisite pam_cracklib.so retry=3 difok=3 minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1’ /etc/pam.d/common-password
fi
fi
Password_Policy=grep "minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1" /etc/pam.d/common-password| grep -v ^#|awk '{print $4","$5","$6","$7","$8}'
if [ -z $Password_Policy ];then
echo “…[N] Password Policy: Reset failed”
else
echo “…[Y] Password Policy: $Password_Policy”
fi
}
#检查日志服务CentOS
function CheckLogService_CentOS() {
Log_Service=systemctl status rsyslog | grep active | awk '{print $3}'
if [ $Log_Service != “(running)” ];then
systemctl start rsyslog
本人从事网路安全工作12年,曾在2个大厂工作过,安全服务、售后服务、售前、攻防比赛、安全讲师、销售经理等职位都做过,对这个行业了解比较全面。
最近遍览了各种网络安全类的文章,内容参差不齐,其中不伐有大佬倾力教学,也有各种不良机构浑水摸鱼,在收到几条私信,发现大家对一套完整的系统的网络安全从学习路线到学习资料,甚至是工具有着不小的需求。
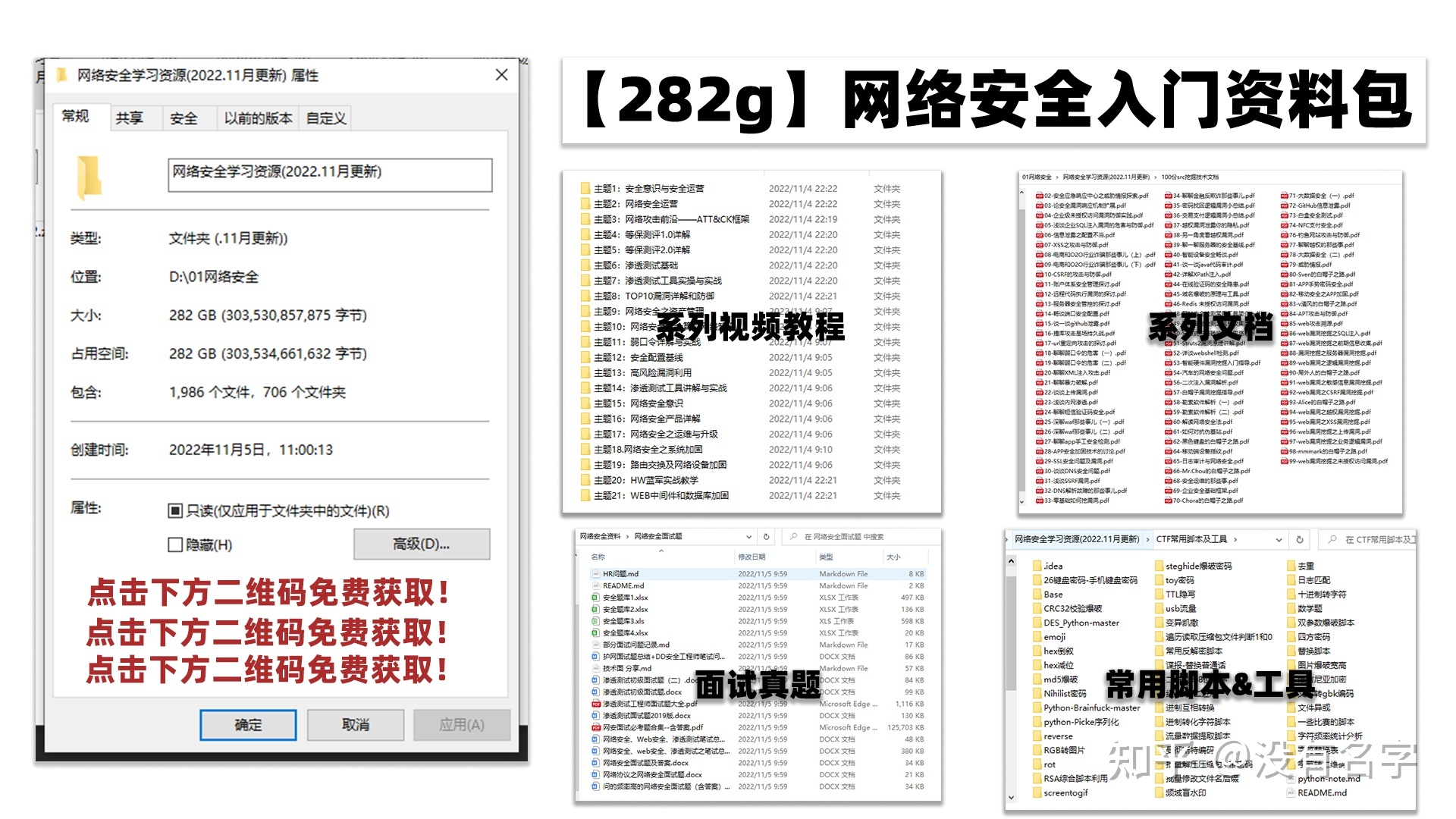
最后,我将这部分内容融会贯通成了一套282G的网络安全资料包,所有类目条理清晰,知识点层层递进,需要的小伙伴可以点击下方小卡片领取哦!下面就开始进入正题,如何从一个萌新一步一步进入网络安全行业。
学习路线图
其中最为瞩目也是最为基础的就是网络安全学习路线图,这里我给大家分享一份打磨了3个月,已经更新到4.0版本的网络安全学习路线图。
相比起繁琐的文字,还是生动的视频教程更加适合零基础的同学们学习,这里也是整理了一份与上述学习路线一一对应的网络安全视频教程。
网络安全工具箱
当然,当你入门之后,仅仅是视频教程已经不能满足你的需求了,你肯定需要学习各种工具的使用以及大量的实战项目,这里也分享一份我自己整理的网络安全入门工具以及使用教程和实战。
项目实战
最后就是项目实战,这里带来的是SRC资料&HW资料,毕竟实战是检验真理的唯一标准嘛~

面试题
归根结底,我们的最终目的都是为了就业,所以这份结合了多位朋友的亲身经验打磨的面试题合集你绝对不能错过!
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
底,我们的最终目的都是为了就业,所以这份结合了多位朋友的亲身经验打磨的面试题合集你绝对不能错过!
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
需要这份系统化的资料的朋友,可以添加V获取:vip204888 (备注网络安全)
[外链图片转存中…(img-Z76by8pm-1713120917262)]
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
